Hello,
In this blog post I’m going to show how to do a trick to bypass the Kaspersky 2018 AV.
For the example, I’m going to use a netcat 99 binary that Kaspersky is going to detect as the following by default: not-a-virus:RemoteAdmin.Win32.NetCat.alj
The AV is doing an static scan, and also a dynamic scan so we are going to need to bypass both. Let’s start for the static one.
In the static scan the AV is going to look for strings that can match his signatures to try to identify the binary, also it can look for hashes or bytes length of the program.
This specific binary has a big code cave and we don’t need to add more bytes with a PE and a hex editor, but I’m going to do it to modify the binary structure.
After doing this we need to encrypt or encode the binary to bypass the static scan. As an example, look at this string when I open the plain text binary in Olly:
This string can match an AV signature and our file can be detected, we should encode it. I’m going to use a really simple encoder because the purpose of this post is not to show you difficult encoding or encrypting techniques.
I’ve already wrote about a bit more complex topics during my SLAE exam, you can find the articles here:
For this specific case, we don’t need a really complex encoder to bypass the AV, so we are going to keep the things simple.
We are doing 3 operation, an addition, an XOR and a subtract.
This is going to be the simple encoder:
And this the decoder, notice the inverse order:
After some trial and error encoding the file, I realized that I needed to encode the text, the rdata and the data section to avoid being detected.
So I implement the encoder to encode the three parts.
Now it’s the moment to scan the file, and Kaspersky doesn’t detect it, but our file doesn’t have the decoder stub. So it seems that we bypassed the static scan of the file.
I leave a 200 Nop sled before the decoder, and I implement the decoder and the registers recovery at the end. The code now is functional:
We scan the file with Kaspersky and it detects it again, with the same signature. It seems that the AV it’s also doing a dynamic scan of the file.
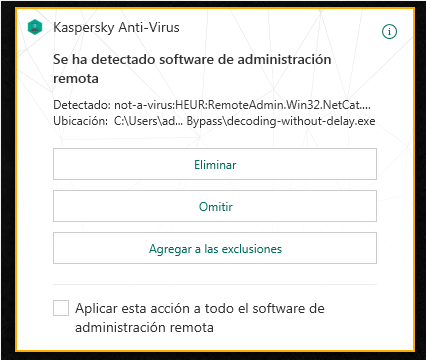
We know that we bypassed the static scan, but how to bypass the dynamic one? I’ve read about this trick in this blog post:
http://blog.noobroot.com/2013/09/bypassing-kaspersky-anti-virus-2014.html
We add a delay to let some seconds pass while AV is scanning the file, we will reach the maximum time scan allowed for scanning a single file and the scan is going to stop. After that the real binary code is going to be executed outside the Kaspersky sandbox.
To do that, we repeat this code 10 times before we execute the binary, in the nop sled that we prepared before:
We are just counting until we reach the value 12341234, and pushing/poping the same value from the stack. These are just some maths operations that are going to cause a delay in the execution of the program.
Now it’s the moment to scan the binary again, and we realize that Kaspersky is not detecting it anymore!
This was just a small trick for this specific AV, but if you want to read some interesting articles about AV bypass I recommend you the following ones:
And that’s all about AV bypass small tricks. See you soon!
