Hello, in this post I will explain how to use execve syscall in a shellcode using the stack technique, the purpose of this shellcode is the same as the last shellcode from the previous post. As I told you in that article, I’m currently studying SLAE certification, and this is a part of the great content of the course.
In this case, we are going to save the data in the stack before moving it to the registers. The data should be saved as multiple of four to get it from the stack using push method.
As you can see the string “/bin/bash” is not a multiple of 4, so we are going to change it to: “////bin/bash”.
The structure that is going to have the stack will be like this, from low memory to high memory:
ECX [////bin/bash address], EDX [0x00000000], EBX ["////bin/bash"], EAX [0x00000000] 1) EAX register:
xor eax, eax
push eax2) EBX will store the “////bin/bash” string. The first thing we need to do is to convert this string to hex, to do this we can use this tool that Vivek Ramachandran shows in the course:
#!/usr/bin/python
import sys
input = sys.argv[1]
print 'String length : ' +str(len(input))
stringList = [input[i:i+4] for i in range(0, len(input), 4)]
for item in stringList[::-1] :
print item[::-1] + ' : ' + str(item[::-1].encode('hex'))You can see in the image below how I used the script to convert the string to hex and put it in the inverse order.
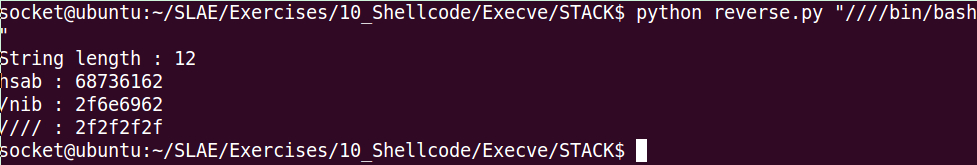
To save this to the stack we need to do 3 pushes, and after we should save the top of the stack to ebx.
push 0x68736162
push 0x2f6e6962
push 0x2f2f2f2f
mov ebx, esp3) A null to EDX
push eax
mov edx, esp4) ECX needs to contain the address of the string
push ebx,
mov ecx, esp5) Invoke the syscall
mov al, 11
int 0x80This is the final Assembly code:
; Filename: execve-stack.nasm
; Author: Vivek Ramachandran
; Website: https://www.pentesteracademy.com
; Student: Xavi Bel
global _start
section .text
_start:
xor eax, eax
push eax
push 0x68736162
push 0x2f6e6962
push 0x2f2f2f2f
mov ebx, esp
push eax
mov edx, esp
push ebx,
mov ecx, esp
mov al, 11
int 0x80I hope this could be useful for someone. See you! 🙂
